Russian WiFi cyber-attack foiled by Dutch intelligence
On October 4, 2018, BBC news https://www.bbc.com/news/world-europe-45747472 reported that an alleged Russian group’s efforts to perform a cyber-attack on the Organisation for the Prevention of Chemical Weapons (OPCW) were foiled by Dutch law enforcement.
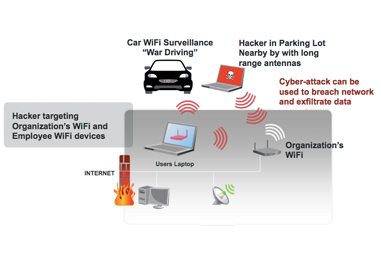
According to the report, the Russians attempted to perform the cyber-attack by weaponizing a rented car by hiding WiFi attack tools and gear in car while parked across the street at a hotel, while also allegedly circling the facility. In the article this was referred to as “close access” and “capturing signals over WiFi antennas”.
The following is a screenshot from the BBC page of the equipment used.

You’ll notice that are a variety of tools common to the WiFi hacking world including long range high-gain WiFi antennas, battery backup and power inverter (common to WiFi “war driving”), and what looks to be a WiFi Pineapple kit (common to WiFi hackers and testing).

Performing a localized cyber-attack such as this is quite easy to conduct. There are a variety of steps that can be performed to attempt to breach a WiFi infrastructure at a facility. This involves targeting both the WiFi access points as well as employee’s devices, including WiFi-enabled laptops, mobile devices and now IoT connected devices.

Let’s explore a list of techniques:
Targeting the WiFi infrastructure and Wireless LAN itself
– Attackers will target the weak points of a WiFi network, these include:- WiFi networks deployed without encryption or those with weak passwords and weak encryption (e.g. WEP)
- WiFi networks that are cryptographically stronger yet still vulnerable to weak passwords and schemes (e.g. WPA-PSK, known common passwords, PSK capture and recovery, WPS-PIN)
- Open Guest network with no password.
- Networks allowing peer-to-peer communication can be leveraged to target other users of that same network, especially employees. If an employee laptop or mobile device is on the Guest network the attacker now has network access to scan the device to identify a vulnerability to exploit.
- Mobile devices, especially jailbroken or rooted devices are low-hanging fruit
- For example, Apple devices have a default built-in admin account – Username: root, Password: alpine. Normally this account is not accessible unless the device is jailbroken. This exposes services such as Secure Shell (ssh) on TCP ports 22 or 2222. If an attacker scans the network and finds an iOS device “and” finds either port open it’s almost a sure bet that the device is jailbroken. Users may not be aware of the default passwords thus never changing them. An attacker can then login as root and gain access to the device and some of its data (this varies based on the iOS version).
- Laptops that don’t have the latest patches can be vulnerable to remote and in-line attacks from tools such as Metasploit, BeEF, sslstrip and others whereby the attacker can identify and exploit vulnerabilities. They can then gather information from the system, plant command and control backdoors and use it a beachhead onto the network to which it’s connected, including any Virtual Private Networks it may connect to.
- In some cases, we’ve found where the Guest network is also accidentally bridged to the Corporate network, thus allowing backdoor access to the entire network

- Targeting employee devices – Beyond targeting employee devices on the Guest network other attack techniques are available:
- Many tools such as Karma, Hostapd-mana, or a WiFi Pineapple can be used to spoof a legitimate network. This could be either the infrastructure’s SSID to lure employees into connecting to this “Evil Twin”
- Another method is to listen to the WiFi networks the device is scanning for. These are previous networks the device had connected to and stored on the device for ease of connectivity as they transition from home to the office to the coffee shop, etc.
- Tools such as Karma, Hostapd-mana or a WiFi Pineapple can be use to respond to these requests, and encourage the employee’s device to connect to this fake network. Once connected, the attacker can then target the local device on his/her hacker network to exploit it and gain access to its data, or use it’s cellular connection to connect to the organization’s network
- A more forceful and similar approach involved sending a deauthentication or disassociate packet (or series of packets) at a connected device to knock it off the organization’s network, and lure the device to connect to the attacker’s fake network because the antenna strength is stronger (a default option in most devices is to connect to the desired network with the strongest antenna strength).
- An newer technique is to target an employee’s mobile device when connected in their car via a WiFi hotspot. Many of these automobile WiFi hotspots are open or have default passwords (there are published lists of these on the web). Attacker can join that same automobile network and use that to target the employee’s mobile device on the same network
While there are even more techniques than what are outlined in this blog, the point here is that this news validates the threat is real and, in this case, the target is a facility that could put people’s lives in danger either directly or indirectly. As the world continues to be more connected through IoT, the wireless attack surface grows greater providing a rich target for attackers. Ensuring your facilities and networks have Wireless Surveillance, Device Fingerprinting, Behavior Analytics, Attack Detections, and multiple layers of protection through Air Isolation, Wireless Deceptive Networking, and Shared Adversarial Intelligence is key to minimizing these threats and avoiding a breach.
The Shared Adversarial Intelligence is key, because blacklists of individuals such as this can be used to identify known bad actors in the vicinity of an organization’s facility is typically the 1st “trip wire” by which an organization can receive an alert of an adversary nearby. This is exactly what we do with our Deceptive Networking at loch for our customers.
Threats such as this also target bluetooth devices and communications. Also, fake cell towers have been documented around the Washington, DC and Las Vegas areas. As demonstrated at the DEF CON hackers conference, standing up a “mini-cell” is quite easy, provide the means to lure cellphones and perform Man-in-the-Middle (MiTM) attacks, and options to downstep signals from LTE to GSM and lower to conduct such attacks. This is something LOCH detects with our AirCell product that’s part of our AirShield sensor and SaaS.
Considering the GRU’s close proximity to OPCW underlines the notion that there is intelligence to be gathered through close access to wireless networks not accessible remotely over the Internet. This alternative approach clearly points out that this could have been a backdoor for access to the wireless network for any company. Adversaries are fully weaponized to perform wireless attacks to gain access to intellectual property, classified data, or fundamentally disrupting the day-to-day operation of an organization by impacting all communications and operations. Ensure you’re prepared to identify any type of adversary looking to breach your wireless networks, whether they be WiFi, Bluetooth, Cellular and more.
