NetShield ACS & rMLS Datasheet
ACS Whitepaper
Key Benefits:
- Agentless Architecture: Deploys without the need for host-based agents, SPAN ports, or intrusive network taps.
- Autonomic Defense: Self-protection and self-healing capabilities minimize human intervention and reduce mean time to detect and respond.
- AI-Driven Anomaly Detection: Advanced AI/ML engines analyze vast wireless and wired data to identify and remediate anomalies in real time.
- Predictive Threat Response: Moves security posture from reactive to proactive with predictive analytics and automated policy enforcement.
Autonomic Cyber Security: Self-Protecting Shield Against AI Cyber Threats
Autonomic Cyber Security (ACS) operates similarly to the human immune system by providing self-protection with minimal or complete absence of user involvement.
It constantly monitors, analyzes, and mitigates anomalous behaviors triggered by attacks, whether known or unknown (for zero-day protection), regardless of location (insider or outsider threats) or cause (natural or malicious).
Its independence allows it to operate without user involvement.
The accelerated adoption of digital transformation, with a connected-everything approach, has created another potential target for cyberattacks. IT systems and ICS/OT systems are no longer separate entities, and using different cybersecurity tools for each system is no longer enough to ensure comprehensive protection.
"Autonomic Cyber Security (ACS) from LOCH Technologies, powered by Data Detection and Response (DDR), enables organizations to securely manage the increasing interconnected systems and combat threats to ensure safety, availability, reliability, and resilience. This comprehensive and coordinated approach guarantees security across the entire cyber-physical risk spectrum, including IT, OT, IoT, IIoT, and physical environments.”
- Professor and Director of the NSF Center for Cloud and Autonomic Computing, Salim Harini, University of Arizona.

Join Us at the Security & Policing Home Office Event – Farnborough, UK, March 11th - 13th, 2025
Read More
Creating the Next Frontier in Wireless Technology: The Critical Need for Wireless Airspace Defense
Read More
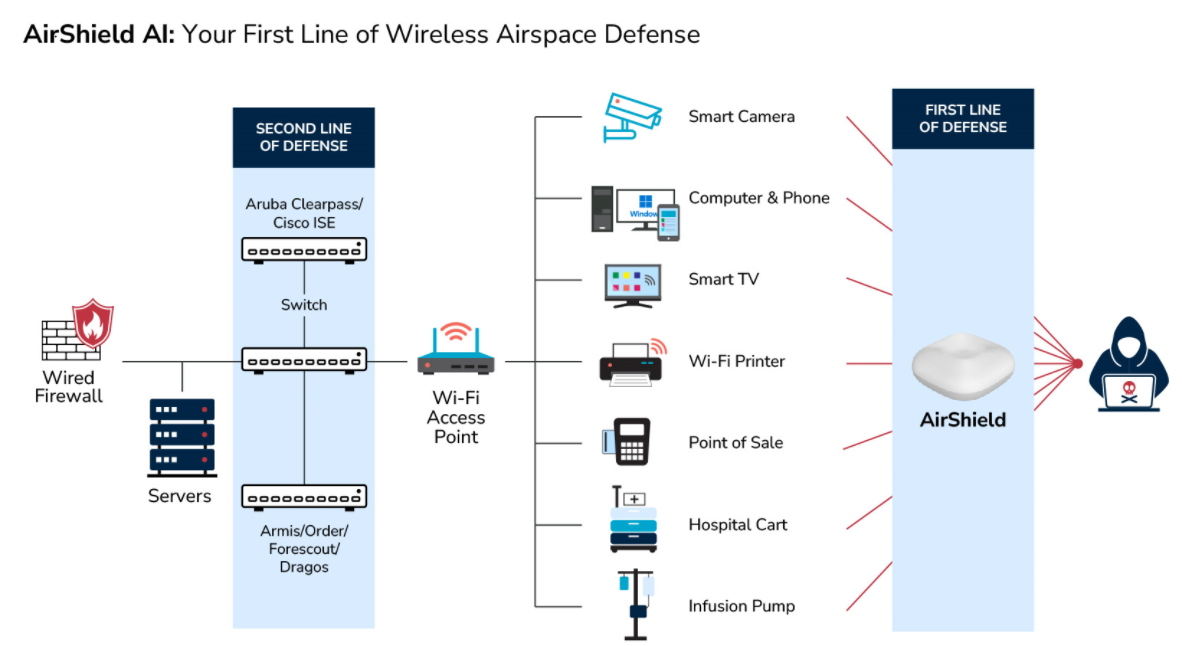
The Silent Threat of Rogue Wi-Fi Networks on Navy Ships – How LOCH's AirShield Could Have Prevented a Security Breach
Read MoreCybersecurity Challenges in Converged IT and OT Environments:
Bridging the Gap for Comprehensive Protection
Digital Transformation Impact
Accelerated adoption of 'Digital Transformation' has connected everything, significantly expanding attack surfaces in ICS/OT environments.
Convergence of IT and OT
IT and ICS/OT systems, once separate, are now integrated. This integration eliminates traditional silos but introduces new cybersecurity challenges.
Inadequacy of Disparate Tools
Traditional cybersecurity tools designed for either IT or ICS/OT systems fail to provide comprehensive protection in converged environments.
Integrated Solutions
There is a critical need for integrated cybersecurity solutions that bridge the gap between IT and OT environments seamlessly. AL/ML Self-Protection provides anomaly behavior analysis of sensors/actuators, applications, protocols users and computing resources.
Risk of Cyber Incidents
Without unified cybersecurity strategies such as AL/ML Self Protection, organizations face increased risks of cyber incidents that could disrupt operations and compromise safety.
Specialized Security Measures
Industrial environments require specialized security measures to mitigate risks effectively while supporting ongoing digital innovation.
Risk of Cyber Incidents
Without unified cybersecurity strategies such as AL/ML Self Protection, organizations face increased risks of cyber incidents that could disrupt operations and compromise safety.
NetShield: Predictive Anomaly Detection You Can Trust to Protect Your Operational Environment
ML driven Anomaly Detection Methodology by predicting ‘datasets’
- Sensors Behavior
- Network Protocol Analysis
- Identity & Access Validations
- Network Behavior
- Applications Behavior
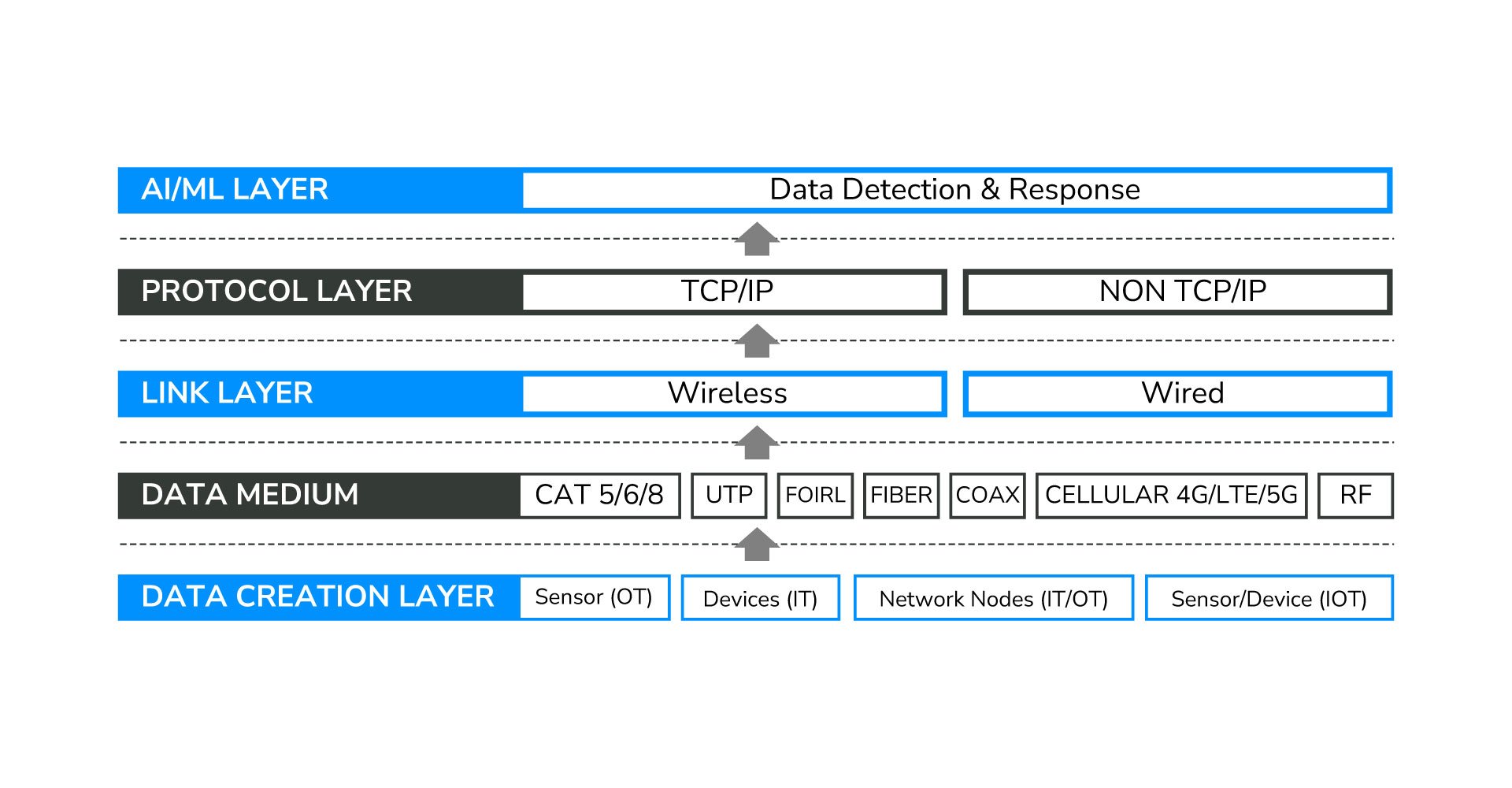
Key Benefits of AI/ML Self-Protection Autonomic Cyber Security
AI / ML Self-Protection
It functions autonomously, much like the human immune system, providing continuous protection without requiring constant user intervention. This is beneficial as it reduces the burden on users and IT staff to manually detect and respond to threats.
Constant Monitoring and Analysis
It continuously monitors and analyzes activities within the network or system. This proactive approach helps in the early detection of anomalous behaviors that could indicate potential cyber threats.
Mitigation of Unknown Threats
It addresses both known and unknown threats, including zero-day attacks. This capability is crucial in today's evolving threat landscape where new vulnerabilities and attack methods constantly emerge.
Versatility in Threat Handling
It responds to threats regardless of their origin (insider or outsider) or nature (natural or malicious). This versatility ensures comprehensive protection against a wide range of cyber threats.
Independence from User Involvement
Its ability to operate independently from user actions means that it can function effectively even in scenarios where users may not be actively engaged or aware of potential threats.
Advanced AI/ML
Autonomic Cyber Security aims to provide robust, automated, and efficient protection against cyber threats, enhancing overall security posture while minimizing the need for continuous human oversight and intervention.
Customer Use Cases
| Feature | Advantage | Benefit |
|---|---|---|
|
Anomaly Behavior Analysis (ABA) of Sensor/Actuator, Applications, Protocols, Users, network and computer resources
|
It is based on using AI/ML algorithm to characterize normal behavior that is available
|
Ability to detect any type of attacks known or unknown. It can be applied to detect accidents/failures that can be trigged by natural or malicious causes
|
|
Automated Attack Type Identification
|
It eliminates the manual intensive effort to identify the attack type, and prioritize the response to the attack
|
It can promptly respond to detected attacks to stop them and mitigate their impacts on normal operations
|
|
Autonomic Incident Response based on Attack Ontology
|
It provides automated approach to characterize the properties of the detected attacks, methods used, vulnerability exploited, and many other relevant properties
|
It provides automated/semi-automated methodology to apply best-practices to response to detected attacks with little or no involvement of users or system administrators
|
Ready to protect using ACS?
About LOCH Technologies
LOCH Technologies, Inc. is a global leader in innovative threat monitoring, detection, and mitigation.
Our cutting-edge ACS solution deliver actionable intelligence on every Device, Network, or Thing, empowering organizations to enhance their security posture and eliminate risk.
At LOCH, our mission is to secure and enable the new world of innovation driving the next generation of digital transformation. We are committed to protecting the digital ecosystem, ensuring a safer and more resilient future for businesses and communities worldwide.