"Invisible" threats at seaports may include digital attacks, insider threats, and other subtle forms of disruption that are not immediately obvious or detectable.
Securing Maritime Operations:
Implementing Robust Wireless Airspace Defense
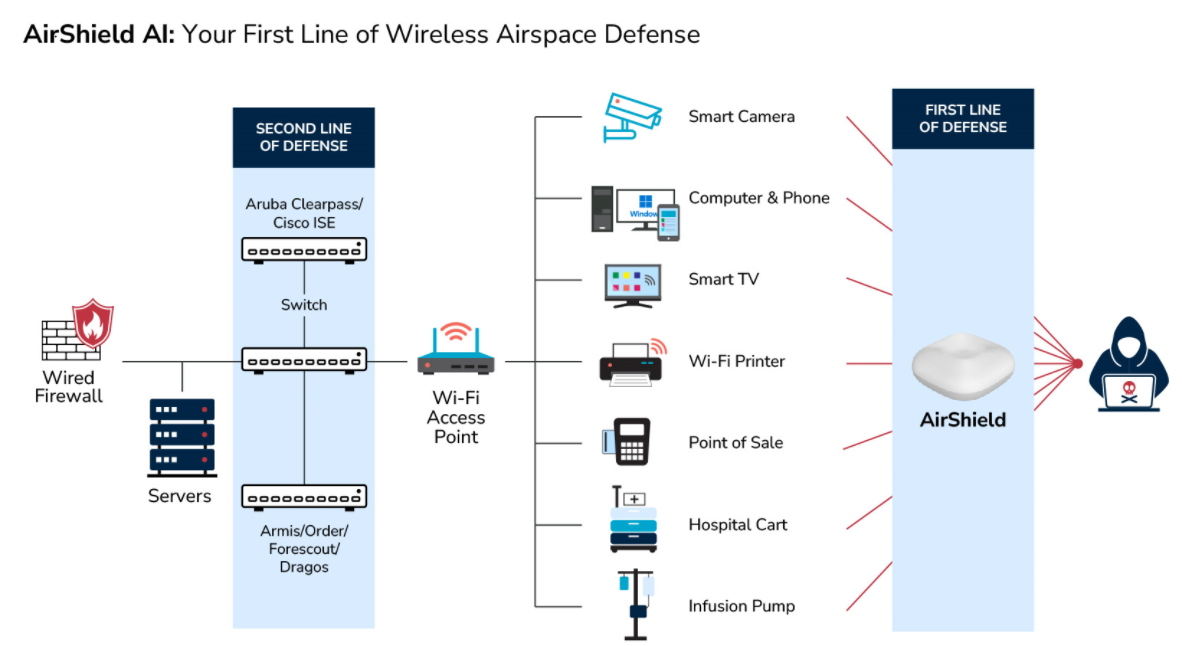
Protect Your Port & Stay Compliant with the Latest USCG Standards
AirShield Wireless Airspace Defense is an intelligent, proactive solution to protect mission-critical wireless networks.
It's a comprehensive security platform that intelligently utilizes state-of-the-art software-defined radios to detect and respond to threats that could compromise wireless signals across critical infrastructure, especially seaport environments.
With this defense system, you can rely on the AirShield wireless security platform to constantly monitor and protect wireless networks from malicious or unauthorized activities.
Through patented AI wireless machine vision, the AirShield wireless airspace defense system will protect and secure mission-critical applications like GPS, Cellular/CBRS, broad-spectrum IoT, and Wi-Fi from emerging new threats.
Securing our Seaports in 2025.
Defending Seaports Against Wireless Airspace Threats.
IoT (Internet of Things)
Threats - Broad-spectrum DDoS, botnet recruitment, firmware exploitation, and MitM attacks.
Impacts - Network infiltration via compromised devices, disabling crucial port systems through botnet activity.
Cellular/CBRS
Threats - Signal jamming, fake cell tower simulators, and SMS phishing.
Impacts - Loss of cellular connectivity and security breaches through phishing, malware distribution, or hijacking.
GPS
Threats - GPS spoofing, jamming, and signal blockage.
Impacts - Incorrect navigation data, disruptions in port logistics and vessel positioning, and delayed response times.
Wi-Fi
Threats - Deauthentification, rogue access points, password cracking and signal jamming
Impacts - Data exfiltration or interception via rogue networks and MitM (Man-in-the-Middle) attacks.
EMI
Threats - Tampered hardware and counterfeit products/chips have found their way on to the motherboard via the supply chain, creating new exposure states.
Impacts - EMI attacks can also covertly exfiltrate sensitive information or intellectual property from your organization.

Join Us at the Security & Policing Home Office Event – Farnborough, UK, March 11th - 13th, 2025
Read More
Creating the Next Frontier in Wireless Technology: The Critical Need for Wireless Airspace Defense
Read More
The Silent Threat of Rogue Wi-Fi Networks on Navy Ships – How LOCH's AirShield Could Have Prevented a Security Breach
Read MoreTo mitigate risk, we recommend implementing the following strategies:
Comprehensive Security Monitoring
Implement network-wide surveillance to detect unusual traffic and patterns across all wireless frequencies.
Encryption and Authentication
Strengthen authentication mechanisms and use strong encryption across wireless communication protocols.
Staff Training
Educate employees about phishing, rogue access points, and secure usage of port IoT devices.
Physical Security
Restrict physical access to critical infrastructure, deploy advanced surveillance systems, enforce multi-layered authentication, and conduct regular security audits to prevent unauthorized entry.
It's crucial to take proactive measures to ensure the safety and security of seaports, and implementing these mitigation strategies will help to prevent potential cyber attacks and keep the port infrastructure safe and secure.
Securing Seaports: The Need for Wireless Airspace Defense
Wireless Intrusion Detection System (WIDS)
Location Tracking
Closing the incident response gap to within 1 inch means that incidents are delivered to the on-site team.
This allows the information security and physical security teams to work together to assess wireless and IoT risks such as spy cameras, rogue wireless networks, unmanaged IoT devices, and Shadow IoT.
Why You Need Wireless Airspace Defense
Increased Wireless Threats
With more IoT devices and wireless communication protocols, ports and facilities are increasingly vulnerable to interception, signal jamming, and unauthorized access.
Blind Spots in Traditional Security
Conventional firewalls and network security tools often miss threats in wireless signals outside their detection scope, leaving the airspace around an organization vulnerable.
Data Integrity and Privacy
Protects sensitive data by ensuring unauthorized devices cannot connect to or intercept communications over wireless networks.
Operational Continuity
Minimizes disruptions to critical operations caused by interference or attacks, ensuring systems remain operational.
Compliance and Safety
Helps organizations meet security standards and guidelines, which are particularly important in critical infrastructure sectors.
- - Detect, identify and classify all broad spectrum RF emitting devices in range
- - Device and network pairing communication map analysis and correlation
- - Risk assessment threat ranking for Zero Trust network access control
- - Mobile App for hunting rogues even if mobile
- - Wireless deep packet inspection
- - Behavioral baselining, analysis and anomaly detection/alerts
- - DVR-like capabilities for forensics, including geo-positioning
- - Carrier integration with cell. devices for anomaly detection, fraud/theft and cost management
- - List and map devices on dashboard or into SIEMs.
- - Interact with MDM and EMM assets for correlation and feedback on exceptions
- - Rectify network segmentation via interactions with SOAR, FW and/or NAC systems
- - Automate response and closure via collaboration with ITSM/ITSL and CMDBs