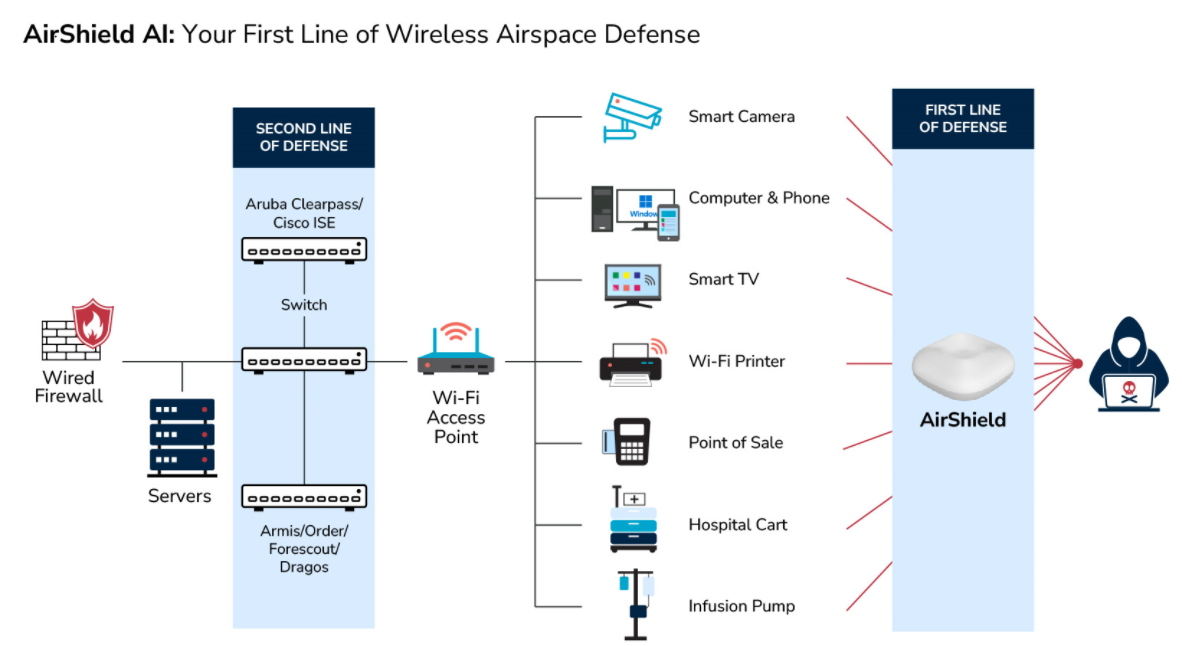
Water and sewage treatment facilities increasingly rely on wireless technologies such as Wi-Fi, Cellular, IoT, CBRS (Citizens Broadband Radio Service), and GPS to maintain and enhance operational efficiency, monitoring, and control. These technologies facilitate hyper-connectivity and support mission-critical services essential for the safe and effective treatment of water and sewage. However, the integration of these technologies also introduces various wireless risks.
LOCH’s Wireless Airspace Defense provides a robust, comprehensive solution to detect, assess, and prevent these risks, ensuring secure and reliable communications.
By leveraging advanced monitoring, threat assessment, and automated response capabilities, LOCH helps water and sewage treatment facilities protect their mission-critical wireless infrastructure, maintain operational continuity, and safeguard against potential security incidents.
Wireless Risks and Threats in Water and Sewage Treatment Facilities
Interference and Jamming
Wi-Fi and Cellular Networks: Unintentional or deliberate interference or jamming of Wi-Fi and cellular signals can disrupt communication between monitoring systems, sensors, and control centers, potentially leading to delays or errors in data transmission.
CBRS: The CBRS spectrum, shared among different users, can be susceptible to interference or deliberate jamming, affecting the reliability of communications.
GPS: GPS jamming or spoofing can affect the accuracy of location-based services, such as the coordination of mobile units or automated systems.
Unauthorized Access and Intrusions
Wi-Fi Networks: Unauthorized access to Wi-Fi networks could allow attackers to manipulate or disrupt control systems, monitor sensitive communications, or exfiltrate data.
IoT Devices: Many IoT devices used in water and sewage treatment are not designed with robust security measures, making them vulnerable to unauthorized access, manipulation, or use as a foothold in the broader network.
Cybersecurity Attacks
Man-in-the-Middle (MitM) Attacks: Attackers can intercept and alter communications between devices and control systems, leading to data manipulation, system disruption, or unauthorized control.
Ransomware and Malware: Wireless networks can serve as entry points for malware and ransomware, potentially leading to system outages, data loss, or manipulation of treatment processes.
Physical Threats to Wireless Infrastructure:
Damage to Infrastructure: Physical damage or sabotage to wireless infrastructure (such as cellular towers or Wi-Fi access points) can disrupt essential communication links, impacting remote monitoring and control capabilities.
Signal Degradation in Harsh Environments
Environmental Factors: Harsh environments (e.g., moisture, chemicals, and physical barriers in treatment facilities) can degrade wireless signals, leading to reduced reliability and potential communication failures.

Join Us at the Security & Policing Home Office Event – Farnborough, UK, March 11th - 13th, 2025
Read More
Creating the Next Frontier in Wireless Technology: The Critical Need for Wireless Airspace Defense
Read More
The Silent Threat of Rogue Wi-Fi Networks on Navy Ships – How LOCH's AirShield Could Have Prevented a Security Breach
Read MorePotential Impacts on Business Operations
Operational Disruptions
Communication Disruptions: Loss of wireless communication can result in operational downtime, particularly in automated monitoring and control systems, leading to inefficiencies and increased manual intervention.
Safety Risks
Compromised Monitoring Systems: If monitoring systems and sensors are compromised, it could result in inaccurate data being used for decision-making, potentially leading to safety hazards such as chemical spills, overflow events, or other operational failures.
Financial Losses
Increased Operational Costs: Downtime, breaches, or system manipulation could result in significant financial losses due to halted operations, emergency responses, and regulatory fines.
Reputational Damage
Public Safety Concerns: Incidents involving compromised water and sewage treatment processes can result in negative publicity and damage public trust, especially if safety or compliance is impacted.
Regulatory Non-Compliance
Data Breaches and Manipulation: Unauthorized access or data breaches can result in the manipulation of data or system settings, leading to non-compliance with regulatory standards and potential fines or penalties.
How LOCH Wireless Airspace Defense Can Mitigate Risks
Continuous Wireless Monitoring
Real-Time Detection: LOCH’s solution offers continuous monitoring of the wireless airspace to detect unauthorized devices, rogue access points, and interference. This real-time detection capability helps to identify and mitigate threats before they can impact operations.
Threat Assessment and Prioritization
Automated Threat Analysis: The system categorizes and prioritizes detected threats based on their potential impact on the facility’s operations. This enables rapid response to critical threats and minimizes the potential for operational disruptions.
Automated Alerts and Mitigation
Immediate Response Capabilities: Automated alerts and pre-configured response actions (such as quarantining devices or adjusting network configurations) help prevent unauthorized access or interference, maintaining the integrity of mission-critical systems.
Integration with Existing Security Systems
Enhanced Situational Awareness
Visibility Across All Wireless Technologies: By providing comprehensive visibility into all wireless activities (Wi-Fi, Cellular, IoT, CBRS, and GPS), LOCH enhances situational awareness, allowing for proactive identification and mitigation of potential threats.
Adaptive Defense Mechanisms
Dynamic Security Adjustments: The solution uses adaptive algorithms to adjust security measures based on the detected threats and the dynamic environment of a treatment facility, ensuring continuous protection and minimizing the risk of disruption.
Compliance Support and Reporting
Regulatory Compliance Assurance: LOCH’s Wireless Airspace Defense provides detailed logs and reports of all wireless activities and security incidents, aiding in regulatory compliance and facilitating audits.
- - Detect, identify and classify all broad spectrum RF emitting devices in range
- - Device and network pairing communication map analysis and correlation
- - Risk assessment threat ranking for Zero Trust network access control
- - Mobile App for hunting rogues even if mobile
- - Wireless deep packet inspection
- - Behavioral baselining, analysis and anomaly detection/alerts
- - DVR-like capabilities for forensics, including geo-positioning
- - Carrier integration with cell. devices for anomaly detection, fraud/theft and cost management
- - List and map devices on dashboard or into SIEMs.
- - Interact with MDM and EMM assets for correlation and feedback on exceptions
- - Rectify network segmentation via interactions with SOAR, FW and/or NAC systems
- - Automate response and closure via collaboration with ITSM/ITSL and CMDBs