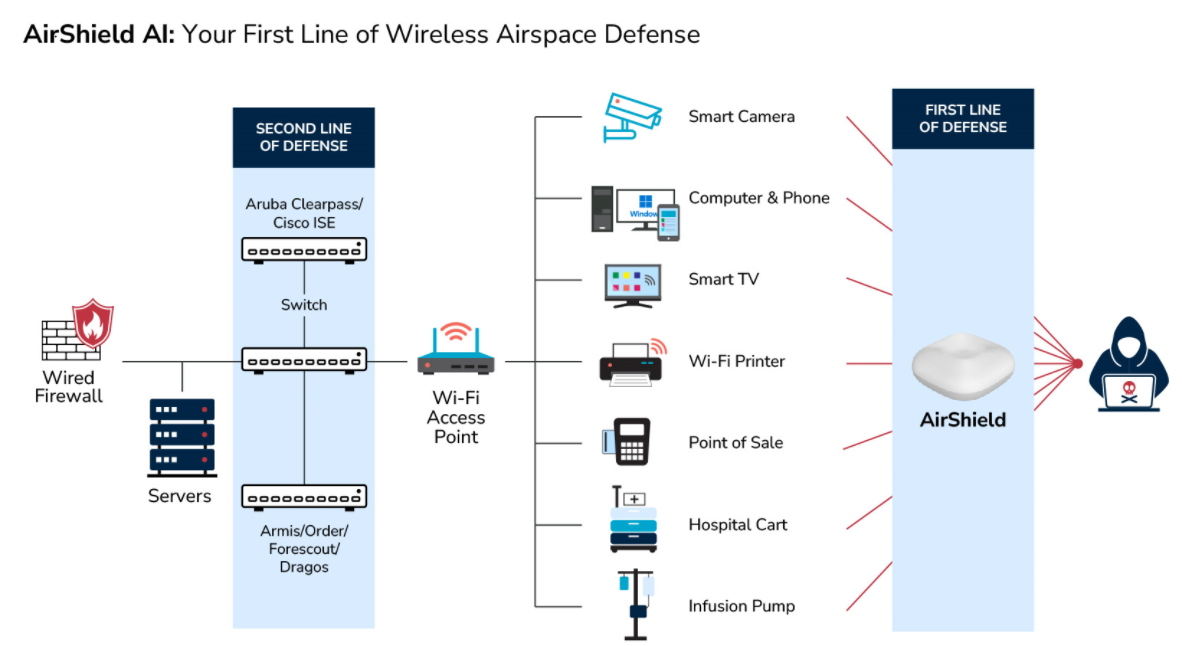
LOCH’s Wireless Airspace Defense provides a robust solution for the oil and gas industry to mitigate wireless risks effectively. By leveraging advanced AI and machine learning for real-time detection, assessment, and response, LOCH ensures that oil and gas companies can maintain secure and reliable communications across downstream and upstream production pipelines, protect critical infrastructure, and operate safely in an increasingly connected and digital environment.

Join Us at the Security & Policing Home Office Event – Farnborough, UK, March 11th - 13th, 2025
Read More
Creating the Next Frontier in Wireless Technology: The Critical Need for Wireless Airspace Defense
Read More
The Silent Threat of Rogue Wi-Fi Networks on Navy Ships – How LOCH's AirShield Could Have Prevented a Security Breach
Read MoreWireless Risks and Threats Impacting Oil and Gas Production
Unauthorized Access and Data Breaches
Threat: Hackers could gain unauthorized access to wireless networks used in oil and gas operations, intercepting sensitive data such as production levels, pipeline conditions, or proprietary technologies.
Impact: Data breaches could lead to the loss of intellectual property, trade secrets, and sensitive operational data, potentially resulting in financial losses and reputational damage.
Wireless Signal Jamming and Denial of Service (DoS) Attacks
Threat: Malicious actors could deploy jamming devices to disrupt wireless communications, affecting critical systems like remote monitoring, SCADA systems, or emergency response communications.
Impact: Disruption of wireless communication can lead to operational downtime, safety hazards, and delayed response times in emergency situations, potentially causing significant financial and environmental damage.
Rogue Devices and Unauthorized Network Access
Threat: Malicious entities could introduce rogue devices (e.g., unauthorized access points or sensors) into the wireless network to capture data or gain unauthorized access to control systems.
Impact: Rogue devices can compromise network security, leading to potential control over critical infrastructure, manipulation of production data, or unauthorized shutdowns of equipment.
Cyber-Physical Attacks
Threat: Wireless vulnerabilities can be exploited to launch cyber-physical attacks, targeting the physical components of the oil and gas infrastructure, such as pumps, valves, or compressors.
Impact: Such attacks can lead to equipment malfunction, production halts, spills, or explosions, resulting in significant safety hazards, environmental damage, and financial losses.
IoT Device Exploitation and Vulnerabilities
Threat: Exploitation of vulnerabilities in IoT devices used in oil and gas operations, such as sensors, cameras, or wearable devices.
Impact: Exploited devices could provide unauthorized access to networks, leak sensitive data, or be used as entry points for further attacks on critical systems.
Man-in-the-Middle (MitM) Attacks
Threat: Attackers intercept wireless communications between devices and network infrastructure, altering or stealing sensitive data in transit.
Impact: This could lead to data tampering, unauthorized control of equipment, and compromised decision-making due to falsified data.

Join Us at the Security & Policing Home Office Event – Farnborough, UK, March 11th - 13th, 2025
Read More
Creating the Next Frontier in Wireless Technology: The Critical Need for Wireless Airspace Defense
Read More
The Silent Threat of Rogue Wi-Fi Networks on Navy Ships – How LOCH's AirShield Could Have Prevented a Security Breach
Read MorePotential Impacts on Business Operations
Operational Disruption and Downtime
Wireless attacks can disrupt critical communication channels and control systems, leading to unplanned shutdowns, production losses, and costly downtime.
Safety & Environmental Risks
Compromised wireless communications can impact the safety of personnel and the environment, especially if critical safety systems (like gas detection or emergency shutdown systems) are disrupted.
Intellectual Property Theft & Competitive Disadvantage
Breaches that result in the loss of proprietary technologies or trade secrets can erode competitive advantage and lead to market share loss.
Financial & Legal Repercussions
Cyberattacks and data breaches can lead to significant financial losses due to halted operations, legal fines, compensation claims, and the cost of incident response and recovery.
Reputation Damage & Loss of Stakeholder Trust
Security breaches can damage the company’s reputation, leading to a loss of customer and stakeholder trust and potentially impacting stock prices and market value.
Regulatory Compliance Violations
Non-compliance with industry regulations due to compromised wireless security can result in legal penalties, increased scrutiny from regulators, and loss of operational licenses.
How LOCH Wireless Airspace Defense Can Mitigate Risks Across Oil & Gas Production
Real-Time Monitoring and Threat Detection
Capability: Continuous monitoring of wireless signals across various spectrums (e.g., Wi-Fi, cellular, Bluetooth) to detect unauthorized devices, rogue access points, and unusual signal patterns.
Benefit: Enables early detection of potential threats, allowing for immediate response to unauthorized access attempts or abnormal wireless activities.
AI-Driven Anomaly Detection
Capability: Utilizes AI and machine learning algorithms to identify and alert on anomalous behaviors in wireless traffic, such as unusual communication patterns or signal interference.
Benefit: Provides a proactive approach to identifying potential threats before they can exploit vulnerabilities or cause significant damage.
Automated Threat Mitigation & Incident Response
Capability: Automatic response mechanisms to isolate and neutralize detected threats, such as blocking rogue devices or jamming attempts without manual intervention.
Benefit: Rapid threat response minimizes potential impact on operations, reduces downtime, and enhances overall network security.
Enhanced Wireless Policy Enforcement
Benefit: Reduces the risk of unauthorized access and minimizes the likelihood of rogue device exploitation or insider threats.
Integration with Existing Security Systems
Capability: Seamlessly integrates with existing cybersecurity frameworks and infrastructure within the oil and gas industry, providing a comprehensive approach to security.
Benefit: Enhances overall security posture without requiring significant changes to existing systems, ensuring consistent protection across all operational areas.
Comprehensive Reporting & Compliance Support
Capability: Provides detailed reports on wireless activity and incidents, supporting regulatory compliance and post-incident analysis.
Benefit: Helps maintain compliance with industry regulations, reduces the risk of legal penalties, and supports continuous improvement in security strategies.
Protection Against Cyber-Physical Attacks
Capability: Monitors for anomalies that could indicate an attempted cyber-physical attack, such as unauthorized control signals or equipment malfunctions triggered via wireless channels.
Benefit: Helps prevent attacks that could cause physical damage to infrastructure, ensuring the safety of both personnel and the environment.
- - Detect, identify and classify all broad spectrum RF emitting devices in range
- - Device and network pairing communication map analysis and correlation
- - Risk assessment threat ranking for Zero Trust network access control
- - Mobile App for hunting rogues even if mobile
- - Wireless deep packet inspection
- - Behavioral baselining, analysis and anomaly detection/alerts
- - DVR-like capabilities for forensics, including geo-positioning
- - Carrier integration with cell. devices for anomaly detection, fraud/theft and cost management
- - List and map devices on dashboard or into SIEMs.
- - Interact with MDM and EMM assets for correlation and feedback on exceptions
- - Rectify network segmentation via interactions with SOAR, FW and/or NAC systems
- - Automate response and closure via collaboration with ITSM/ITSL and CMDBs