5G Cellular
Attack Surface
What is 5G Cellular?
In this discussion, Gary Drummond elaborates on the essence of 5G technology, its advancements over 4G, and its implications for various sectors, including IoT, autonomous vehicles, and smart cities. The video discusses 5G's capacity for faster data speeds, lower latency, and increased connectivity, which are pivotal for driving innovations and enhancing operations across industries. Additionally, Garry highlights the critical challenges and risks associated with 5G adoption, such as cybersecurity vulnerabilities, supply chain risks, and privacy concerns, underscoring the necessity for businesses to adopt robust security measures and risk assessments to navigate these challenges effectively.
Garry Drummond, CEO and Founder of LOCH, explains the opportunities presented by 5G and the risks that can come with this exciting technology

Join Us at the Security & Policing Home Office Event – Farnborough, UK, March 11th - 13th, 2025
Read More
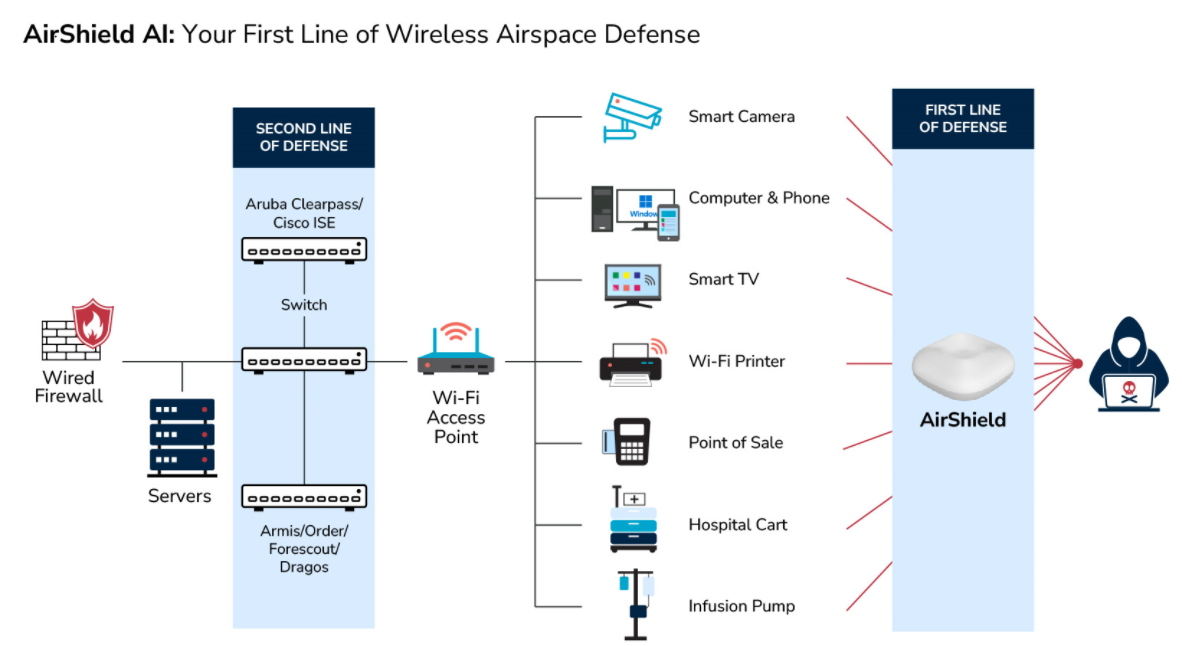
Creating the Next Frontier in Wireless Technology: The Critical Need for Wireless Airspace Defense
Read More
The Silent Threat of Rogue Wi-Fi Networks on Navy Ships – How LOCH's AirShield Could Have Prevented a Security Breach
Read MoreThe Risks and Threats to 5G

Unique risks and threats are associated with the adoption of 5G technology, with specific cybersecurity vulnerabilities, such as, supply chain risks, and privacy concerns. It is important to understand the increased potential for cyber attacks due to the enhanced speeds and connectivity of 5G networks, as well as the expanded attack surface created by the massive number of connected devices. Learn how to protect your organization in our comprehensive data sheet.
How do we protect against 5G risks and vulnerabilities?
LOCH's AirShield platform addresses the evolving risks and threats associated with 5G by providing comprehensive RF surveillance and threat monitoring across various technologies, including 5G cellular, CBRS, IoT, Bluetooth, and Wi-Fi. Utilizing software-defined radio technology for asset discovery, classification, and exposure state identification, AirShield enables customers to proactively manage vulnerabilities and protect their wireless networks through advanced air termination capabilities.
LOCH secures wireless 5G vulnerabilities through
Software Defined Radio
Provides asset discovery, classification, highlight exposure states, and prioritize threats
RF Surveillance
Monitoring all available wireless frequencies to surveil all your wireless systems
Wireless Mitigation Capability
Over-the-air mitigation, through air termination
Manual and Automated Threat Response
AirShield offers both manual and automated measures to respond to an identified response