WiFi Attack Surface
WiFi: Benefits, Risks and Security Needs
Organizations around the world are increasingly turning to wireless systems to run their businesses. WiFi is quite possibly the most widely used of these systems, but can be one of the most vulnerable if proper precautions are not taken. Garry Drummond, our Founder and CEO talks about all things WiFi, offering advice and insights for organizations on how to securely and safely leverage WiFi in their company.
Garry Drummond, Founder and CEO of LOCH, explains WiFi, its functionality, and the risks for organizations

Join Us at the Security & Policing Home Office Event – Farnborough, UK, March 11th - 13th, 2025
Read More
Creating the Next Frontier in Wireless Technology: The Critical Need for Wireless Airspace Defense
Read More
The Silent Threat of Rogue Wi-Fi Networks on Navy Ships – How LOCH's AirShield Could Have Prevented a Security Breach
Read MoreRisks and Threats to WiFi
Garry Drummond explains the threats and risk of WiFi
Wireless technologies, while offering numerous benefits, also introduce a range of risks and threats such as unauthorized access, eavesdropping, man-in-the-middle attacks, denial of service attacks, rogue access points, SSID spoofing, weak encryption, physical security risks, and vulnerabilities in Bluetooth and NFC. To mitigate these risks, organizations and individuals should implement robust security measures including encryption, authentication, access control, intrusion detection systems, and conduct regular security audits of their wireless networks and devices.
Examples of WiFi Threats
Eavesdropping
Unauthorized access that intercepts sensitive information
Man-in-the-middle
Intercept and alter the communications between a device and the network
Denial of Service
Target specific individual users or entire networks, overloading them with traffic to degrade or disrupt service
Rogue Access Points
SSID Spoofing
How do we protect against WiFi threats and vulnerabilities?
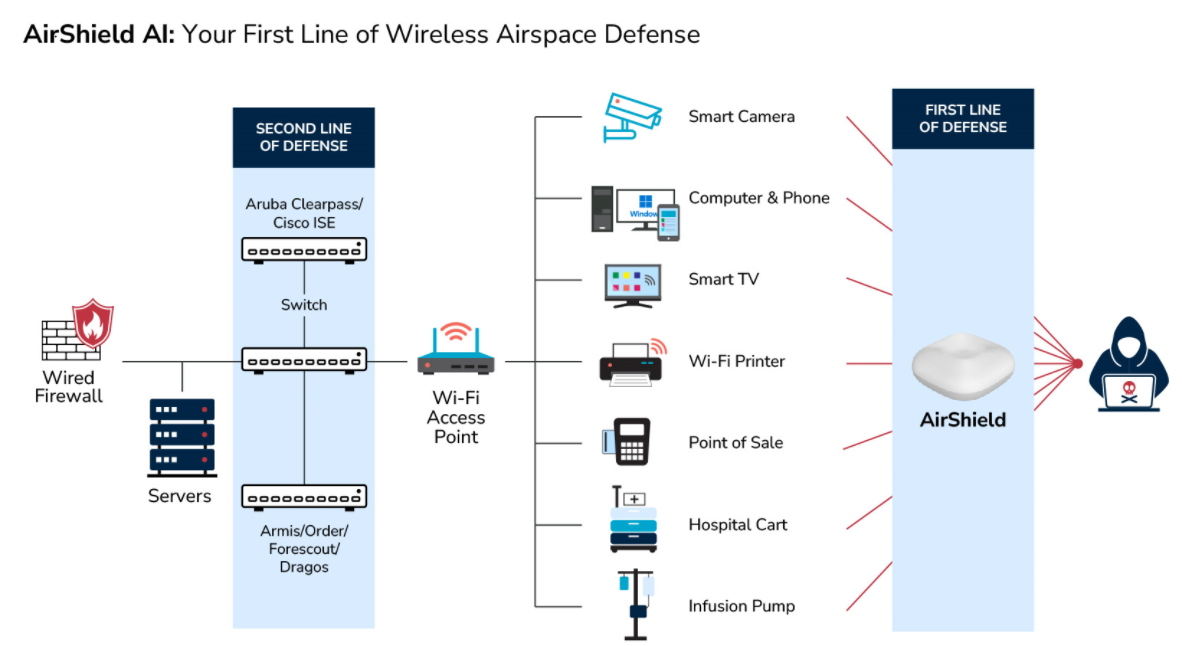
LOCH provides innovative solutions to combat wireless security threats through our AirShield platform, offering customers comprehensive visibility of their environment and dynamic adaptation to various frequencies and protocols. AirShield enables an independent audit of findings, prioritizes risks by severity for targeted action, and facilitates mitigation capabilities, thereby allowing organizations to effectively manage and neutralize wireless security risks across an ever-changing landscape.
Garry Drummond explains how to secure your WiFi network
LOCH solves WiFi security issues through
Wireless Audit
Risk Prioritization
Triaging risks by prioritizing them based on severity of targeted action
Mitigation Capabilities
Mitigating the vulnerabilities to limit exposure
Proactive Response
Solutions provided immediately and in order of severity based on the prioritization