Internet of Things (IoT)
Attack Surface
IoT: Opportunities, Threats and Security Needs
The Internet of Things (IoT) is revolutionizing how organizations do business. From increasing efficiency, to monitoring maintenance, to enhancing communications, IoT devices are helping companies in a host of ways. Garry Drummond, LOCH Founder and CEO talks about all things IoT, offering advice and insights for organizations on how to securely and safely leverage IoT networks in their business.
Garry Drummond, Founder and CEO of LOCH, explains IoT, its business applications, and the risks for organizations

Join Us at the Security & Policing Home Office Event – Farnborough, UK, March 11th - 13th, 2025
Read More
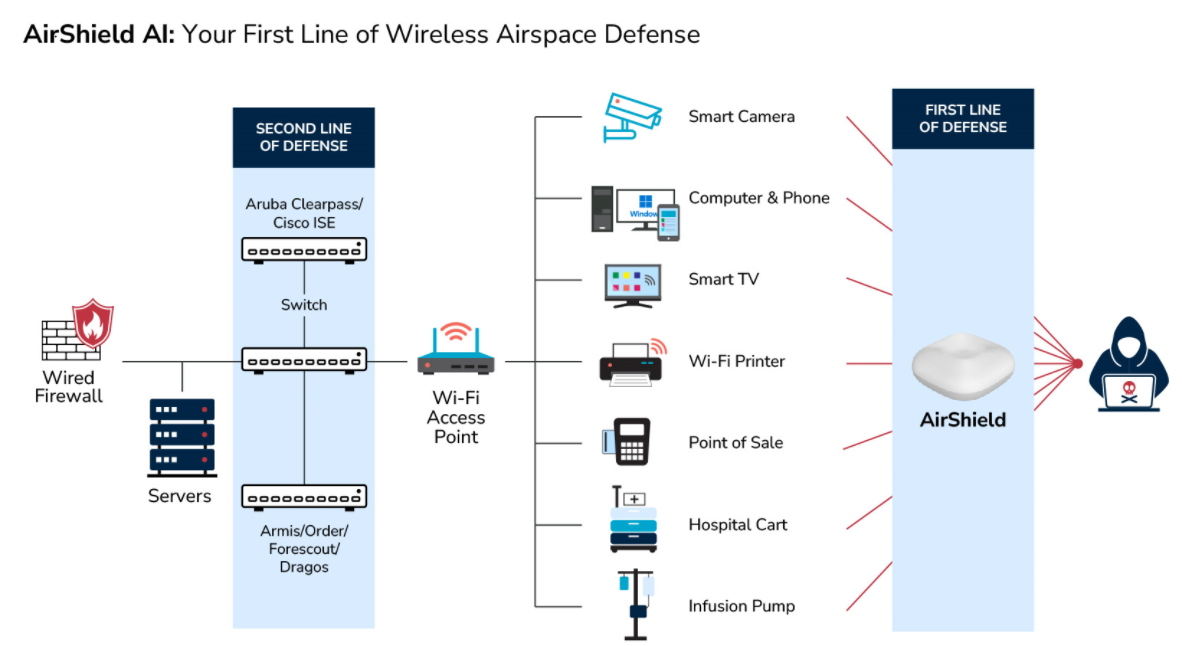
Creating the Next Frontier in Wireless Technology: The Critical Need for Wireless Airspace Defense
Read More
The Silent Threat of Rogue Wi-Fi Networks on Navy Ships – How LOCH's AirShield Could Have Prevented a Security Breach
Read MoreRisks and Threats to the IoT
IoT devices have inherent weaknesses due to limited CPU and storage capabilities, making them prone to unauthorized access and attacks exploiting weak or default passwords. Additionally, issues like weak authentication, insecure communication channels, lack of security updates, and physical vulnerabilities, can cause security issues.
Examples of IoT Threats
CPU Limits
IoT devices are designed for specific functions, not complex computing
Unauthorized Access
If not properly configured, IoT protocols may be breached with relatively simple methods
Password Hacking
Many users do not employ unique passwords for their IoT devices making them vulnerable to hacking
Rogue Access Points
Small Storage Capacity
Lack of Authentication and Updates
IoT devices require proper authentication and updates, just like anything else on a network. Failing to consider this leaves IoT devices, and by default your entire network vulnerable
How do we protect against IoT threats and vulnerabilities?
To mitigate IoT security risks, it's crucial to implement robust authentication, use strong passwords, and employ secure communication protocols like SSL/TLS. Additionally, segmenting IoT devices into different networks based on their risk levels and continuously monitoring for threats can significantly enhance security. Data Detection and Response (DDR) technologies are also recommended for early detection of potential attacks, helping to prevent them before they can cause harm.
LOCH solves IoT security issues through
Wireless Assessment
Network Segmentation
Properly segmenting all your wireless devices increasing your overall security
Continuous Monitoring
24x7 monitoring and response for your entire wireless network
DDR Protocol
Data Detection and Response protocols and firewalls protect your information and data