Bluetooth
Attack Surface
Bluetooth is now being used for mission-critical applications.
Any disruption or delay could impact a variety of daily functions.
What is the Bluetooth attack surface?
Bluetooth uses short-range radio waves to connect devices within the Industrial, Scientific, and Medical (ISM) bands.
Bluetooth has had an exciting evolution from audio streaming to critical RF/Wireless applications due to enhancements in security and mesh capabilities.
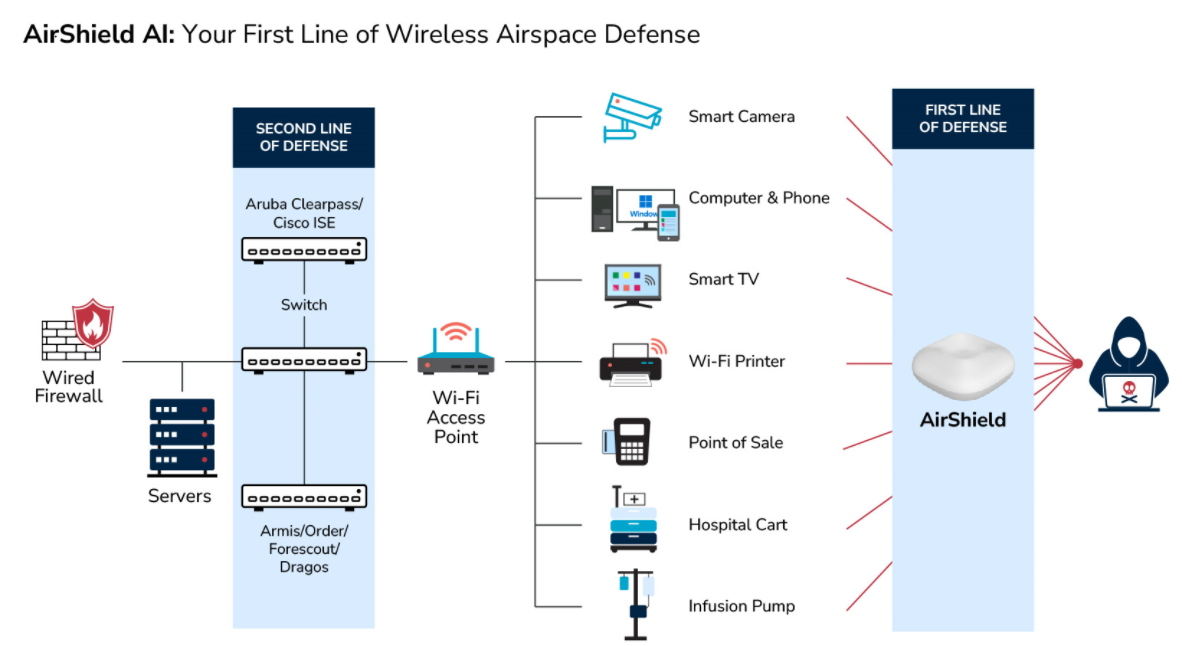
To protect against Bluetooth's vulnerabilities, risks need to be eliminated through strong authentication, secure communication protocols, network segmentation, and continuous wireless threat monitoring.
Garry Drummond, Founder and CEO of LOCH, explains Bluetooth, threats for organizations, and how to prevent Bluetooth security incidents

Join Us at the Security & Policing Home Office Event – Farnborough, UK, March 11th - 13th, 2025
Read More
Creating the Next Frontier in Wireless Technology: The Critical Need for Wireless Airspace Defense
Read More
The Silent Threat of Rogue Wi-Fi Networks on Navy Ships – How LOCH's AirShield Could Have Prevented a Security Breach
Read MoreWireless Airspace Defense for Bluetooth
Bluejacking
Attackers send unsolicited files to Bluetooth-enabled devices for spamming or social engineering attacks
Spoofing
Attackers are able to impersonate legitimate Bluetooth devices to gain unauthorized access to devices in network
BlueBorne Attacks
Set of vulnerabilities allowing attackers to execute man-in-the-middle type attacks on the data stream impacting multiple Bluetooth devices
Denial of Service (DOS) Attacks
Attackers can disrupt service operations by launching DoS attacks via Bluetooth
Ready to protect against Bluetooth attacks?
Protecting Against Bluetooth Attacks
To enhance Bluetooth security, implement strong authentication with unique passwords, utilize SSL and TLS for secure data transmission, and segregate RF/Wireless devices into distinct network zones.
Continuous monitoring platforms, such as LOCH's AirShield, play a critical role in detecting and mitigating evolving risks associated with Bluetooth communication.