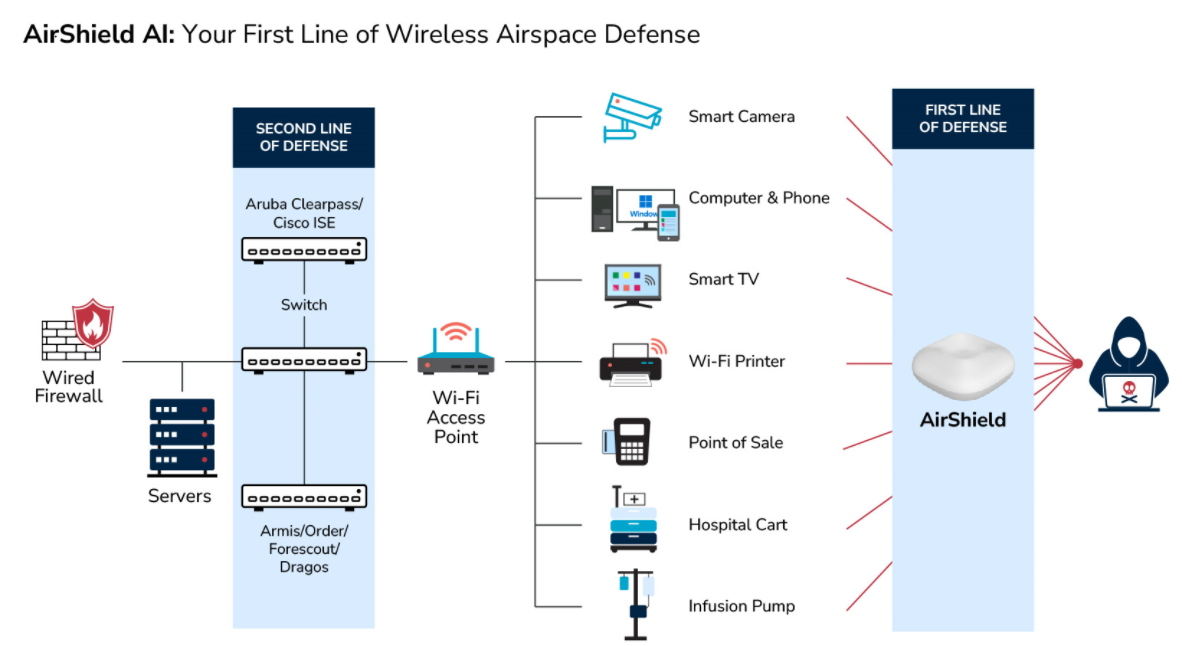
Protect your brand, property, and customers through passive wireless/RF security monitoring of your airspace.
AirShield Wireless Airspace Defense is an intelligent, proactive solution to protect mission-critical wireless networks.
It's a comprehensive security platform that intelligently utilizes state-of-the-art software-defined radios to detect and respond to threats that could compromise wireless signals across critical infrastructure, especially gaming environments.
With this defense system, you can rely on the AirShield wireless security platform to constantly monitor and protect wireless networks from malicious or unauthorized activities.
Through patented AI wireless machine vision, the AirShield wireless airspace defense system will protect and secure mission-critical applications like GPS, Cellular/CBRS, broad-spectrum IoT, and Wi-Fi from emerging new threats.

Join Us at the Security & Policing Home Office Event – Farnborough, UK, March 11th - 13th, 2025
Read More
Creating the Next Frontier in Wireless Technology: The Critical Need for Wireless Airspace Defense
Read More
The Silent Threat of Rogue Wi-Fi Networks on Navy Ships – How LOCH's AirShield Could Have Prevented a Security Breach
Read MoreWhy You Need Wireless Airspace Defense for Gaming
Data Protection
Protect against potential and damaging data loss and breaches
Asset Management
Asset configuration management, visibility, and classification
Threat Mitigation
Mitigate threats through air isolation and deceptive networking
Incident Response
Incident response and forensics through DVR-like capabilities
Continuous Monitoring
Stop wireless attacks in the path with real-time CPE notifications
AirShield: Eliminate the Wireless Security Blind Spot and Protect Your Network

Invisible Threats. Visible Protection.
Make AirShield part of your critical security decision making and protect against the invisible RF espionage threat.
The sheer volume of IoT in the gaming environment has created the world’s largest attack surface. Protect your enterprise business against misconfigurations, Shadow IoT, and unknown and unsecured IoT devices with LOCH Wireless Airspace Defense.
With 80% of IoT wireless, wireless is now the new access layer and new attack surface. Yet most organizations still rely on wired-centric security approaches to detect and assess risk. With LOCH Wireless Airspace Defense, you can better understand and prepare for this new threat landscape.
Take a proactive stance on IoT security with compressive asset discovery and visibility, risk analysis and mitigation, and event detection and response. Moreover, accurately quantify wireless and IoT risks — prior to loss or incidents occurring. LOCH's Wireless Airspace Defense platform follows the industry’s best security practices.
- - Detect, identify and classify all broad spectrum RF emitting devices in range
- - Device and network pairing communication map analysis and correlation
- - Risk assessment threat ranking for Zero Trust network access control
- - Mobile App for hunting rogues even if mobile
- - Wireless deep packet inspection
- - Behavioral baselining, analysis and anomaly detection/alerts
- - DVR-like capabilities for forensics, including geo-positioning
- - Carrier integration with cell. devices for anomaly detection, fraud/theft and cost management
- - List and map devices on dashboard or into SIEMs.
- - Interact with MDM and EMM assets for correlation and feedback on exceptions
- - Rectify network segmentation via interactions with SOAR, FW and/or NAC systems
- - Automate response and closure via collaboration with ITSM/ITSL and CMDBs