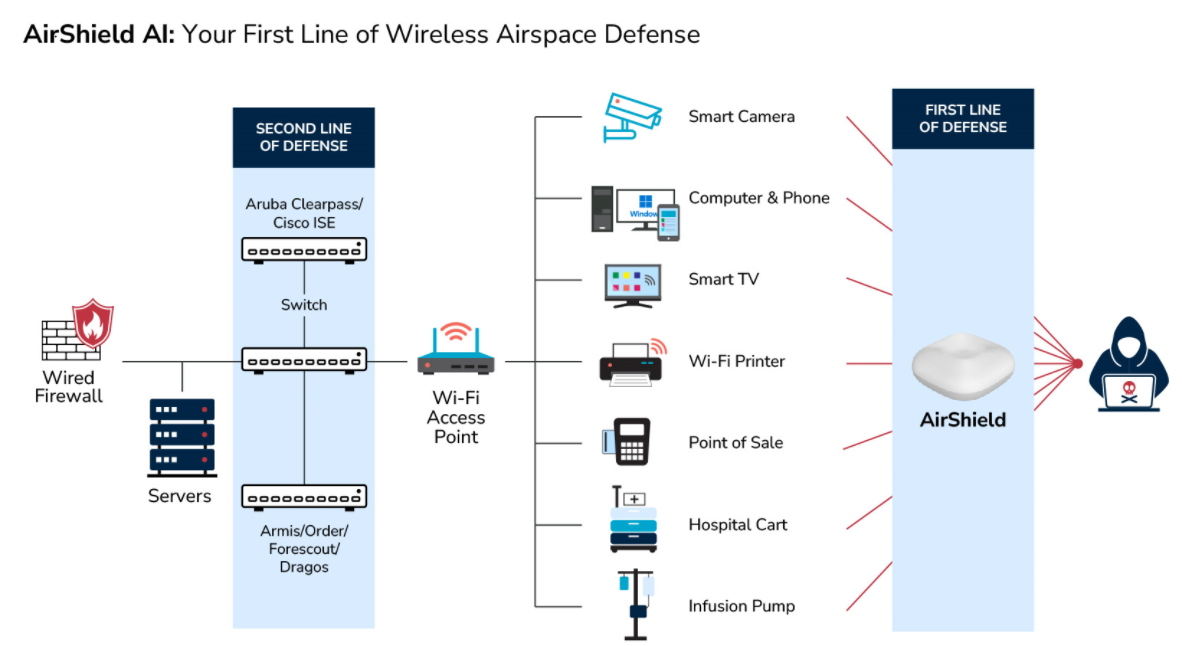
Impacted Attack Surfaces
The invisible nature of wireless networks allows threats to travel through the air, making them harder to detect and mitigate. Without real-time visibility into these protocols, organizations are left exposed to data breaches, espionage, and operational disruptions.

Join Us at the Security & Policing Home Office Event – Farnborough, UK, March 11th - 13th, 2025
Read More
Creating the Next Frontier in Wireless Technology: The Critical Need for Wireless Airspace Defense
Read More
The Silent Threat of Rogue Wi-Fi Networks on Navy Ships – How LOCH's AirShield Could Have Prevented a Security Breach
Read MoreThe Impact of Non-Compliance with Wireless Security Protocols
Data Breaches and Theft
Non-compliance with wireless security can lead to widespread data breaches, exposing sensitive company data, customer information, or intellectual property. This is particularly dangerous for industries handling confidential information, such as healthcare, finance, or government sectors, where the stakes of data loss are immense.
Regulatory Fines & Legal Penalties
Industries like healthcare (HIPAA), finance (PCI-DSS), and government (NIST) are heavily regulated. Non-compliance with wireless security standards in these sectors can result in severe financial penalties, lawsuits, and even criminal investigations, costing millions in fines and damaging reputations.
Reputation Damage
A breach caused by wireless vulnerabilities can severely harm an organization’s reputation. Loss of customer trust and negative media coverage can lead to a decline in business, long-term reputational damage, and the erosion of client relationships, especially if private data is compromised or if critical services are disrupted.
Operational Disruption
Attacks targeting wireless networks, including GPS jamming or signal interference in critical sectors like transportation or energy, can disrupt operations, causing costly downtime. In industries like manufacturing, logistics, or aviation, this could lead to accidents, missed deadlines, or halted services, impacting revenue and safety.
Physical Damage & Safety Risks
Wireless vulnerabilities in critical infrastructure, such as industrial IoT systems controlling power grids, water treatment plants, or oil rigs, could result in catastrophic outcomes. A wireless cyberattack could manipulate these systems, causing physical damage to equipment, endangering human lives, and triggering large-scale service outages.
National Security Threats
In government or military contexts, non-compliance with wireless security can lead to serious national security risks. Unauthorized wireless access, GPS spoofing, or signal interference can compromise critical communication systems, jeopardize classified data, or disrupt defense operations, leading to espionage or even terrorism risks.
Wireless networks, including Wi-Fi, Bluetooth, GPS, 5G/CBRS, and IoT, represent a multi-access edge of hyper-connectivity that requires constant monitoring and validation. In this new landscape, Zero Trust for Wireless means continuously verifying the identities of devices, inspecting all wireless traffic, and enforcing strict access control measures to secure the invisible edges.
Wireless Airspace Defense mappings to HIPAA, PCI-DSS, and NIST wireless security standards
| NIST Security Standards | LOCH Wireless Airspace Defense Features |
|---|---|
|
Protect Wireless Communications (SP 800-53 SC-40)
|
Real-time monitoring and securing of all wireless protocols including Wi-Fi, IoT, and GPS
|
|
Control Access to Wireless Networks (SP 800-53 AC-18)
|
Zero Trust policies enforcing strict access control across wireless networks
|
|
Monitor Wireless Activity and Detect Anomalies (SP 800-53 CA-7)
|
AI-based detection of wireless anomalies and rogue devices
|
|
Ensure Secure Wireless Device Configuration (SP 800-53 CM-8)
|
Automated configuration checks and security enforcement for wireless devices
|
|
Incident Response and Continuous Wireless Monitoring (SP 800-53 IR-4)
|
Real-time incident detection and automated response to wireless security threats
|
| PCI-DSS Security Standards | LOCH Wireless Airspace Defense Features |
|---|---|
|
Ensure Confidentiality, Integrity, and Availability of ePHI (164.306)
|
Real-time monitoring of wireless devices to ensure no unauthorized access to ePHI
|
|
Implement Device and Media Controls (164.310)
|
Control of rogue devices and unauthorized wireless access points
|
|
Access Controls for Mobile Devices and Wireless Systems (164.312)
|
Enforce Zero Trust policies across wireless networks and devices
|
|
Audit Controls and Monitoring (164.312)
|
Continuous auditing and AI-driven threat detection to monitor wireless activity
|
|
Transmission Security for Wireless Communication (164.312(e)(1))
|
Encryption and secure transmission for wireless data, preventing unauthorized interception
|
| HIPAA Security Standards | LOCH Wireless Airspace Defense Features |
|---|---|
|
Install and Maintain a Secure Wireless Network (Requirement 1, 2)
|
Multi-protocol wireless coverage including Wi-Fi, IoT, and 5G
|
|
Protect Cardholder Data Across Wireless Channels (Requirement 3, 4)
|
Real-time visibility and encryption to protect cardholder data over wireless networks
|
|
Implement Strong Access Control Measures (Requirement 7, 8, 9)
|
Zero Trust enforcement and rogue device detection
|
|
Regularly Monitor and Test Wireless Networks (Requirement 10, 11)
|
AI-driven threat detection and continuous monitoring for wireless vulnerabilities
|
|
Maintain an Information Security Policy (Requirement 12)
|
Comprehensive reporting to support security policies and regulatory compliance
|
Key Threats Facing Hyper-Connected Wireless Ecosystems
Device Spoofing
Attackers impersonate legitimate devices to gain access to sensitive networks.
Bluetooth Exploits
With the rise of Bluetooth devices, attackers can exploit vulnerabilities in smartphones, wearables, and IoT devices to gain unauthorized access.
GPS Spoofing
Cybercriminals manipulate GPS signals, disrupting location-based services in critical sectors like aviation and transportation.
5G/CBRS Eavesdropping
With the widespread adoption of 5G and CBRS, cellular eavesdropping and unauthorized access become major concerns.
EMI Attacks
Electromagnetic interference (EMI) can disrupt wireless communication channels, providing a means for attackers to create security gaps.
The Invisible Threat: Securing the Expanding Wireless Attack Surface
Industry Solutions for IT, IoT, And OT Security

Government
Unauthorized wireless access in government facilities can compromise national security, public safety, and operational integrity, leading to espionage or critical service disruptions.

Healthcare
Medical IoT devices, patient monitoring systems, and wireless medical records systems are prime targets. A breach in this sector can lead to catastrophic outcomes, including HIPAA violations and even loss of life.

Transportation
GPS jamming or signal interference in aviation, shipping, and public transportation can cause dangerous accidents and disrupt critical services.

Utilities
Industrial IoT devices in power grids and oil rigs are susceptible to wireless cyberattacks, which can lead to service outages or even physical damage to infrastructure.
The LOCH Wireless Airspace Defense Platform
LOCH is at the forefront of securing the multi-access edge with its Wireless Airspace Defense Platform. The platform provides comprehensive real-time visibility, AI-driven insights, and automated responses across wireless protocols, ensuring organizations are protected from these invisible threats.
Real-Time Monitoring
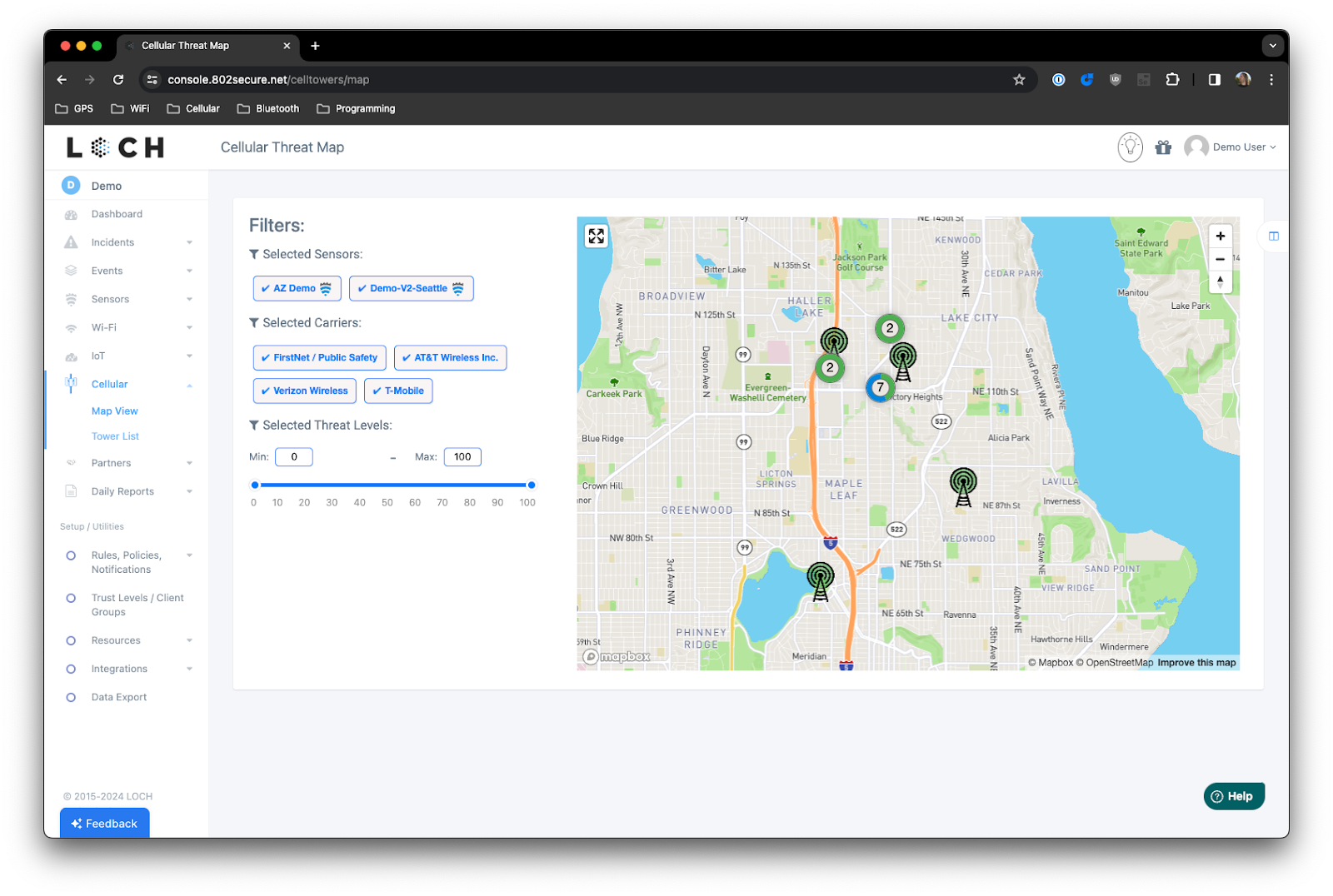
LOCH offers real-time visibility of all wireless devices and communications, from IoT sensors to smartphones and drones, ensuring rogue or unauthorized devices are quickly identified.
AI-Driven Threat Detection
The platform uses AI to analyze wireless signals, detecting anomalies like signal interference, unauthorized device connections, or network compromises.
Multi-Protocol Coverage
Unlike traditional cybersecurity solutions, LOCH’s platform secures a broad range of wireless technologies, including Wi-Fi, IoT, GPS, cellular (4G/5G), and CBRS, providing comprehensive protection.
Automated Response
LOCH's platform not only detects threats but can take automated actions to neutralize them, whether by blocking rogue devices or alerting security teams in real-time.
Protecting the Invisible Edge: A New Era of Wireless Security
Traditional network security tools, such as firewalls and antivirus software, fall short in addressing the unique challenges posed by wireless threats. LOCH bridges this gap by focusing on Wireless Airspace Defense:
Real-Time Alerts & Remediation:
The AI-driven engine sends real-time alerts and takes proactive measures, such as isolating rogue devices, to stop threats before they escalate.Rogue Device Detection
LOCH scans wireless environments for unauthorized devices, preventing them from infiltrating sensitive networks.Signal Interference Prevention
By monitoring GPS jamming, Wi-Fi interference, and cellular disruptions, LOCH ensures continuous and secure wireless communication.
The Future of Wireless Security
As wireless connectivity continues to grow with 5G, IoT, and smart infrastructure, the demand for comprehensive wireless security will only increase. LOCH is positioned at the forefront of this shift, offering a scalable and future-proof platform to secure the hyper-connected world of tomorrow.