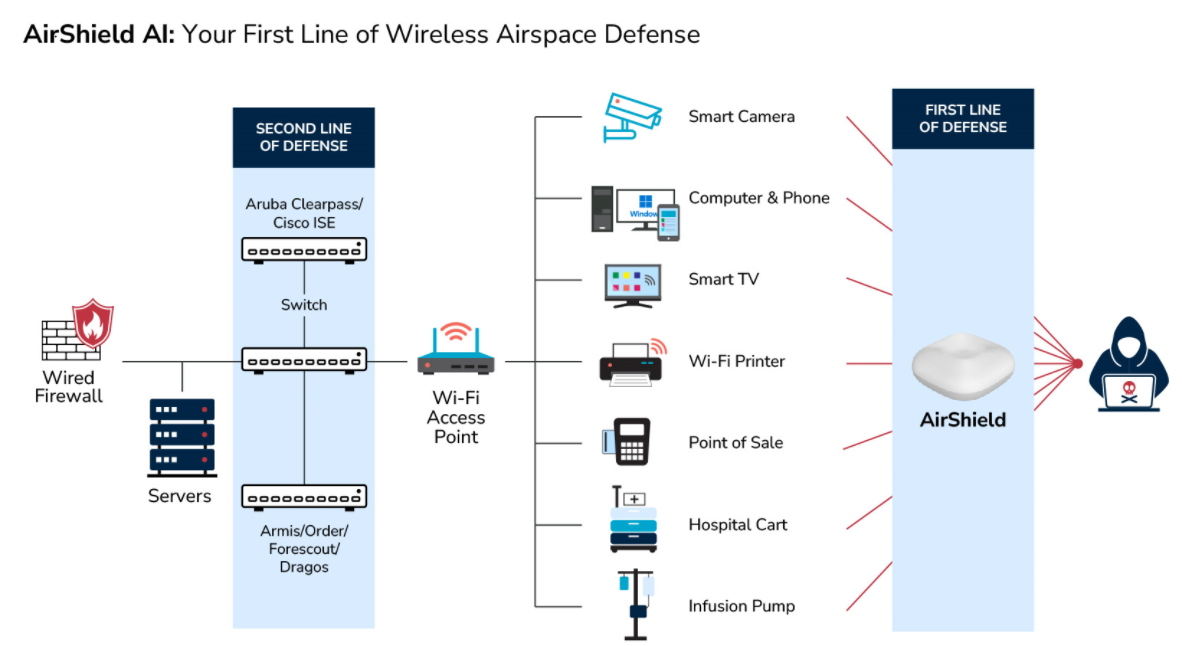
The Hidden Dangers: Exposing "Invisible" Threats Across Mission-Critical Infrastructure
AirShield for all Devices, Things, and Networks
Invisible Threats. Visible Protection.
The rapid expansion of connected devices is surpassing human capacity and the capabilities of traditional security solutions to maintain a secure environment. AI and ML-enabled RF awareness and spectrum monitoring are essential for detecting, evaluating, and preventing risks from 'hidden' threats. Access our new whitepaper on Wireless Airspace Defense for a comprehensive understanding of this evolving threat landscape.
AI and ML-based methods for asset discovery, classification, and risk profiling through edge-based risk management of this new external attack is only possible through DDR (data detection and response) and software-defined radios (SDRs).
Visibility
Discover all broad-spectrum wireless devices, IoT things and Networks within your environment
Protection
Automatically identify unmanaged, unsecured, and misconfigured IT, IoT, and OT entities
Non-Intrusive
Passive monitoring of airwaves for enforcement of Zero Trust policies
Easy to Deploy
Choice of multiple deployment options - on-premise, cloud, or direct-to-browser and with or without LAN connectivity makes it easy for fast access to real-time threat-hunting analytics.
The Power of AI-Enabled Signal Intelligence
The increase in Wireless/RF devices has created a visibility challenge. The proliferation of wireless technology has introduced numerous new operating systems, protocols, and frequencies that are unknown and new to cyber security personnel, making it difficult to manage and protect this new attack surface.
With AirShield, organizations can now proactively identify and categorize all emitting RF devices, enabling them to detect, assess, and prevent risks.

HVAC (Heating, Ventilation and Cooling)

Wireless Thumb Drivers

Voice Assistants

Laptops & Servers

Surveillance Cameras

Drones

Smart TVs

Wireless Printers

Spy Cameras

Cellphone & Tablets

Rogue Cell Towers

Join Us at the Security & Policing Home Office Event – Farnborough, UK, March 11th - 13th, 2025
Read More
Creating the Next Frontier in Wireless Technology: The Critical Need for Wireless Airspace Defense
Read More
The Silent Threat of Rogue Wi-Fi Networks on Navy Ships – How LOCH's AirShield Could Have Prevented a Security Breach
Read MoreAirShield Solution
AirShield℠ offers non-intrusive real-time visibility, comprehensive monitoring, and protection for a wide range of wireless devices in IoT, Industrial Internet of Things (IIOT), Internet of Medical Things (IOMT), and OT environments. It works seamlessly regardless of the operating system, protocol, or connection type.

Cloud-Enabled
AirShield℠ sensors connect to the LOCH Technologies Machine Vision Cloud. Optional server installation is available. Receive real-time and actionable results in minutes, easily integrate with your daily SIEM/SOARs operations.
Real-time Data Analytics
Identify unacceptable wireless IT, IoT, and OT vulnerabilities on managed and unmanaged devices, things, and networks. Close the incident response loop with AirShield’s Threat Hunting Incident Tracker app.
Customizable Software-Defined Radio
Software-Defined Radio monitors the new WiFi 6 and 5G spectrum (300Mhz to 6Ghz) to detect new and advanced wireless IoT threats.
Critical Path to Exposure™ Reporting
Raise awareness of the growing IT, IoT, and OT security risks. Leverage the industry’s leading wireless/RF security benchmark to measure how well you’re doing.
Mobile Threat Hunting Application
As part of AirShield’s solution, a mobile threat-hunting application is provided to locate and remove offending entities in the environment.
-
AirShield
Uncover Hidden RF Threats:
The Power of Proactive RF Threat Hunting
Connect / Sign On
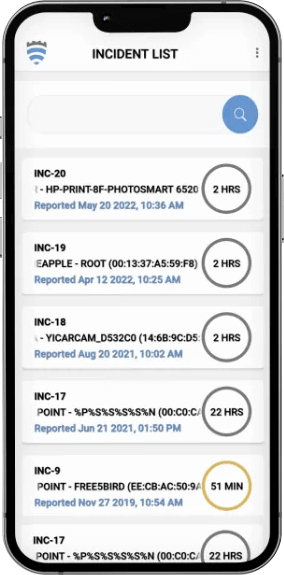
Incident List
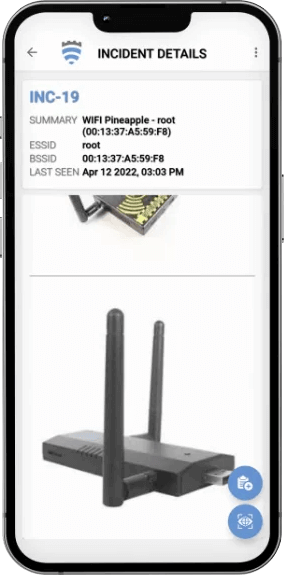
Incident Details
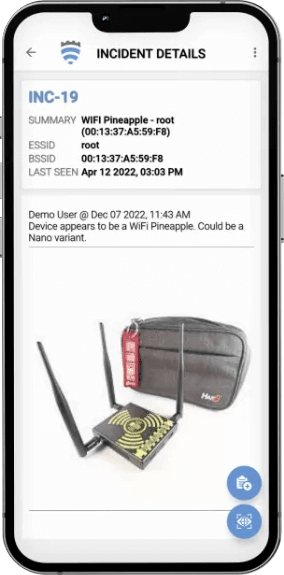
Incident Details
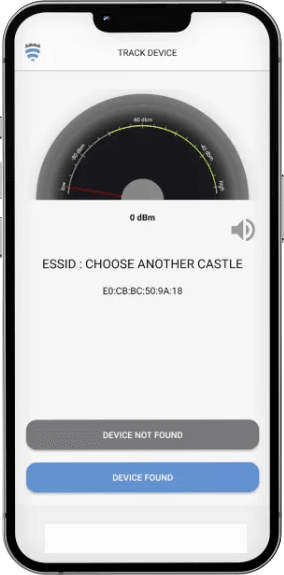
Track Device
- - Detect, identify and classify all broad spectrum RF emitting devices in range
- - Device and network pairing communication map analysis and correlation
- - Risk assessment threat ranking for Zero Trust network access control
- - Mobile App for hunting rogues even if mobile
- - Wireless deep packet inspection
- - Behavioral baselining, analysis and anomaly detection/alerts
- - DVR-like capabilities for forensics, including geo-positioning
- - Carrier integration with cell. devices for anomaly detection, fraud/theft and cost management
- - List and map devices on dashboard or into SIEMs.
- - Interact with MDM and EMM assets for correlation and feedback on exceptions
- - Rectify network segmentation via interactions with SOAR, FW and/or NAC systems
- - Automate response and closure via collaboration with ITSM/ITSL and CMDBs
LOCH Technologies Wireless Cybersecurity Solutions
Resources

Sales Partners
The Support You Need To Successfully Deploy Solutions From LOCH Technologies
Technology Partners
The Integrations That Make Successful Deployments Possible.