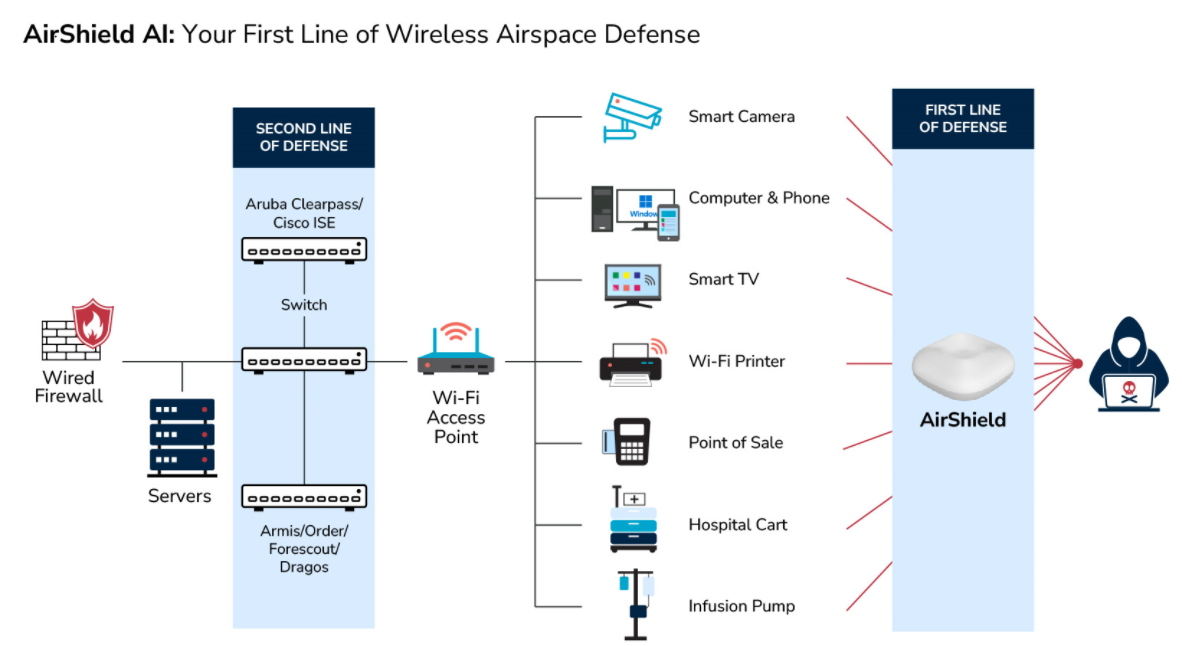
Proactive, Intelligent Wireless Fencing – detect, assess, and prevent risk for IoT devices.
IoT has created the world’s largest attack surface, and the sheer volume of IoT enablement in retail environments has created new risks for organizations.
Retailers must now contend with the invisible RF espionage threat of unsecured and misconfigured Shadow IoT, as well as unknown Zero-day IoT attacks.
Only through the use of LOCH’s Wireless Airspace Defense platform can you detect, assess and prevent risk across new wireless frequencies like LORA, SigFox, and Bluetooth, which are currently in retail use.
Wireless is now the new network. Retailers are now using smart devices and numerous wireless technologies to communicate, including LTE, 5G, broad-spectrum IoT, CBRS as well as satellite communications, making them even more vulnerable to cyber-attacks.
POS attacks have been common in the past, but new attacks on inventory management and supply chain at data centers or warehouses can be catastrophic.

Join Us at the Security & Policing Home Office Event – Farnborough, UK, March 11th - 13th, 2025
Read More
Creating the Next Frontier in Wireless Technology: The Critical Need for Wireless Airspace Defense
Read More
The Silent Threat of Rogue Wi-Fi Networks on Navy Ships – How LOCH's AirShield Could Have Prevented a Security Breach
Read More
Strengthening National Security with LOCH AirShield Wireless Airspace Defense and ACS - Autonomic Cybersecurity: Mitigating the Risks of Chinese Maritime Cranes
Read More
Advancing the Future of Cybersecurity with Resilient Machine Learning Systems (rMLS) to Protect Artificial Intelligence and Machine Learning from Cyberattacks
Read MoreCybersecurity Vulnerabilities of Wireless Retail Systems
POS Attacks
POS or “point-of-sale” attacks are especially popular with cyber criminals, because the POS system contains some of the most sensitive data possible — the card numbers and PINs of the company’s customers.
Web Application Attacks
Attackers will attempt to breach a company’s online payment application, then install malicious code designed to steal the customer’s credit card information as they enter it.
Weak Authorization
Retail networks may be set up to use (WPS) WiFi Protected Setup. As a result, access codes to many devices are well known or easily brute-forceable, which allows an attacker access to the network.
Insider Threats
As always, these are a common threat to retail companies, as employee turnover can be high and there are points of vulnerability
Cookie Theft / Sidejacking / Session Hijacking
A cookie theft is exactly what it sounds like: a hacker exploits an insecure connection to steal your cookie and pretend that they’re you on the website you’re visiting.
Weak Encryption
Retail networks may not follow strong and required network security practices by using common/easily recovered WPA/WPA2 passphrases, or unencrypted or known weak networks.
Fake/Rogue Cell Tower
As wireless devices may have cellular access, an attacker may want to ensure cellular access is unavailable while performing Wi-Fi attacks. To accomplish this, they create fake cell towers and deny authentication to the network.
Rogue Devices
A rogue device, such as a spy camera, wireless-enabled USB drive, or an open printer may put the remote home user/network at risk.
Downgrade Cellular Network
Attacks against weaker cellular networks require disabling more secure networks, allowing for man-in-the-middle attacks or enabling them to install trojans.
- - Detect, identify and classify all broad spectrum RF emitting devices in range
- - Device and network pairing communication map analysis and correlation
- - Risk assessment threat ranking for Zero Trust network access control
- - Mobile App for hunting rogues even if mobile
- - Wireless deep packet inspection
- - Behavioral baselining, analysis and anomaly detection/alerts
- - DVR-like capabilities for forensics, including geo-positioning
- - Carrier integration with cell. devices for anomaly detection, fraud/theft and cost management
- - List and map devices on dashboard or into SIEMs.
- - Interact with MDM and EMM assets for correlation and feedback on exceptions
- - Rectify network segmentation via interactions with SOAR, FW and/or NAC systems
- - Automate response and closure via collaboration with ITSM/ITSL and CMDBs