Real Insights, Real-time Responses to IoT Security Risks.
Smart factories and other manufacturing facilities play a critical role in today’s society.
Robotics and smart sensors use broad-spectrum wireless and cellular to communicate, therefore new visibility is required to detect, assess, and prevent risk.
Only through Wireless Airspace Defense is it possible to accomplish predictive IoT analytics and insights for a best practice and secure network.
80% of new IoT deployments in Manufacturing are now being connected via wireless, yet many companies are still using wired-centric security approaches which are ineffective in securing mission-critical devices and networks.
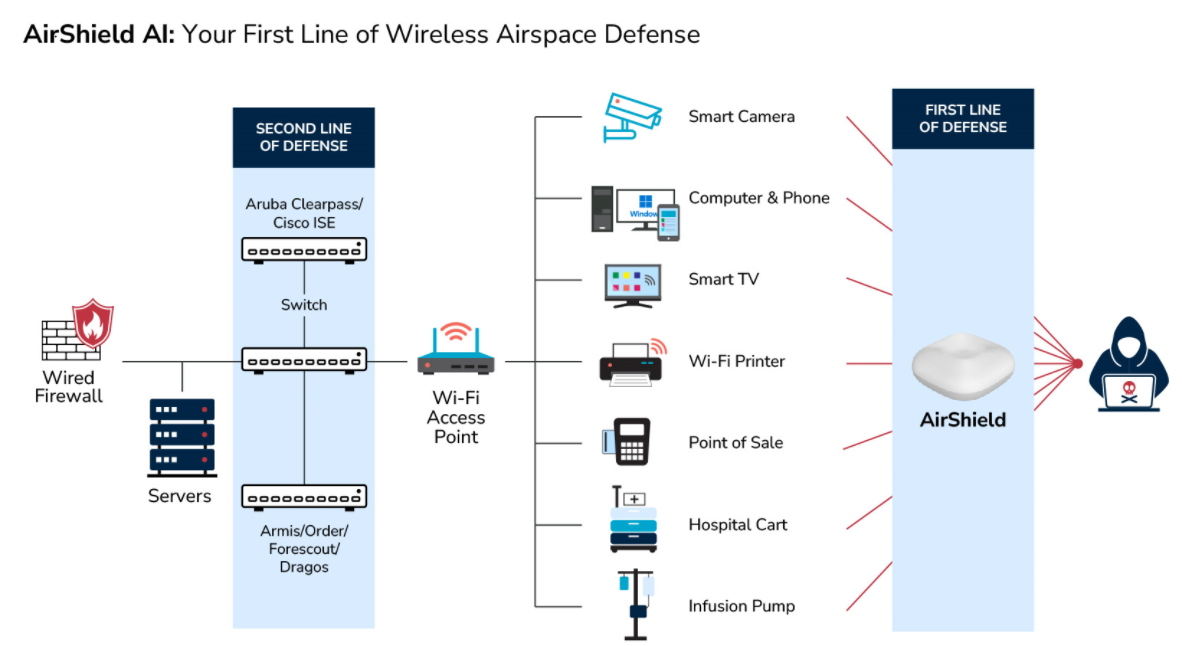
Many existing solutions fail to provide advanced M2M behavior insights including the first line of defense, an alert notification for any deviation of policy; or the second line of defense, which is proactively identifying IoT vulnerabilities prior to loss or incident occurring.

Join Us at the Security & Policing Home Office Event – Farnborough, UK, March 11th - 13th, 2025
Read More
Creating the Next Frontier in Wireless Technology: The Critical Need for Wireless Airspace Defense
Read More
The Silent Threat of Rogue Wi-Fi Networks on Navy Ships – How LOCH's AirShield Could Have Prevented a Security Breach
Read More
Strengthening National Security with LOCH AirShield Wireless Airspace Defense and ACS - Autonomic Cybersecurity: Mitigating the Risks of Chinese Maritime Cranes
Read More
Advancing the Future of Cybersecurity with Resilient Machine Learning Systems (rMLS) to Protect Artificial Intelligence and Machine Learning from Cyberattacks
Read MoreCybersecurity Vulnerabilities of Wireless Manufacturing Systems
Rogue Cell Towers
Attacks on cell towers being attacked from unauthorized devices
Evil Twin Attacks
Unauthorized devices connecting to authorized Wi-Fi Access Points
Roaming
Monitor potential data exfiltration against traffic base line to flag malware and bots.
Device Threats
Malware, Firmware Hacks, Sensor IoT
Compromises, Man In the Middle Attacks, Device Tampering
AirShield for Manufacturing: Business Benefits
Asset Inventory & Visibility
You can’t defend what you can’t see. Therefore, it is crucial to Implement a solution that is dynamically in-tune with your ever-changing OT environment, particularly as IoT converges with OT. With AirShield, you can detect, assess, and prevent risk across your mission-critical manufacturing environments.
Proactive Vulnerability Assessment
Identify and fix unacceptable wireless OT vulnerability exposure states prior to loss or incident occurring. As per the Gartner Market Guide for Operational Technology Security, risk analysis and mitigation is crucial to detect anomalous behaviors and remediate vulnerabilities in dynamic OT environments.
Deploy and Scale Easily
With cloud-based configuration and management, AirShield scales easily to meet the needs of your organization. Get real-time insights across multiple cellular carriers and regions for OT assets and more.
Financial Losses
With broad-spectrum OT and cellular enablement proliferating in many OT environments, you can implement effective cost management and performance monitoring with Wireless Airspace Defense.
- - Detect, identify and classify all broad spectrum RF emitting devices in range
- - Device and network pairing communication map analysis and correlation
- - Risk assessment threat ranking for Zero Trust network access control
- - Mobile App for hunting rogues even if mobile
- - Wireless deep packet inspection
- - Behavioral baselining, analysis and anomaly detection/alerts
- - DVR-like capabilities for forensics, including geo-positioning
- - Carrier integration with cell. devices for anomaly detection, fraud/theft and cost management
- - List and map devices on dashboard or into SIEMs.
- - Interact with MDM and EMM assets for correlation and feedback on exceptions
- - Rectify network segmentation via interactions with SOAR, FW and/or NAC systems
- - Automate response and closure via collaboration with ITSM/ITSL and CMDBs