Proactive, Intelligent Wireless Network Protection.
Wireless is now the new network. Government organizations now use smart devices and numerous wireless technologies to communicate, including LTE, 5G, broad-spectrum IoT, CBRS as well as satellite communications making them even more vulnerable to cyber-attacks.
IoT has created the world’s largest attack surface and the sheer volume of IoT enablement into the government environment has created new risks that organizations need to address.
Government agencies need to protect against the invisible RF espionage threat of unsecured, misconfigured Shadow IoT as well as unknown Zero-day IoT attacks.
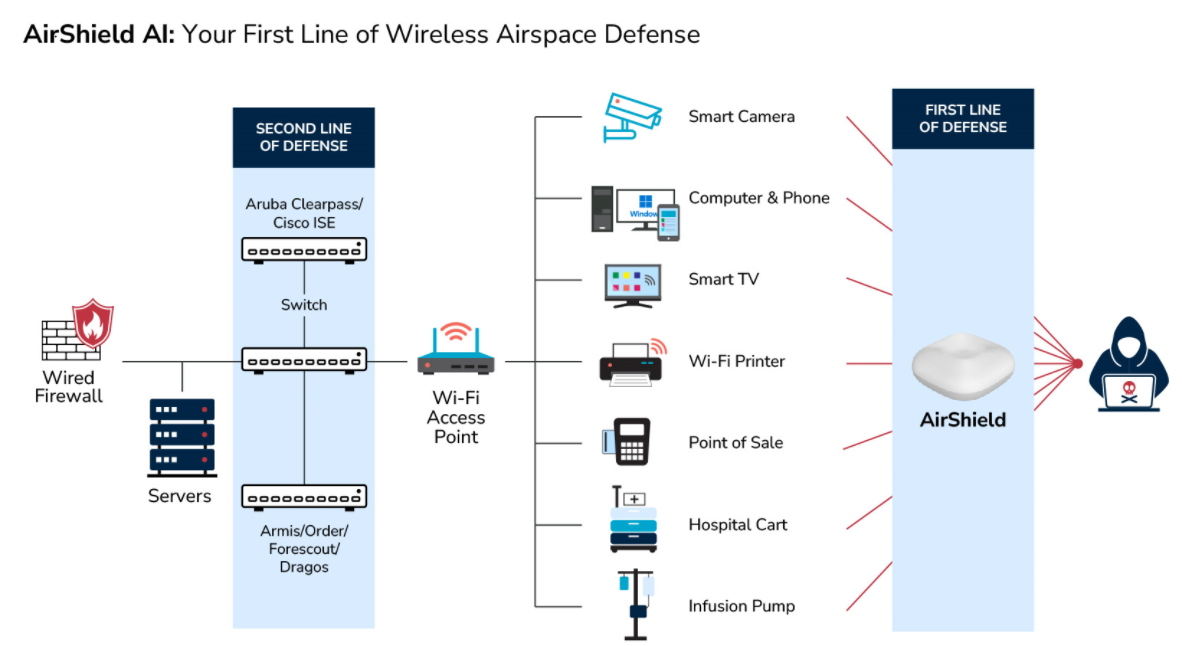
LOCH’s Wireless Airspace Defense Platform can you detect, assess and prevent data exploitation across the full spectrum of wireless frequencies in use.

Join Us at the Security & Policing Home Office Event – Farnborough, UK, March 11th - 13th, 2025
Read More
Creating the Next Frontier in Wireless Technology: The Critical Need for Wireless Airspace Defense
Read More
The Silent Threat of Rogue Wi-Fi Networks on Navy Ships – How LOCH's AirShield Could Have Prevented a Security Breach
Read More
Strengthening National Security with LOCH AirShield Wireless Airspace Defense and ACS - Autonomic Cybersecurity: Mitigating the Risks of Chinese Maritime Cranes
Read More
Advancing the Future of Cybersecurity with Resilient Machine Learning Systems (rMLS) to Protect Artificial Intelligence and Machine Learning from Cyberattacks
Read More
Wireless Airspace Defense Capabilities
Resilient Machine Learning Systems (rMLS) Capabilities

Detect
- - Detect, identify and classify all broad spectrum RF emitting devices in range
- - Device and network pairing communication map analysis and correlation
- - Risk assessment threat ranking for Zero Trust network access control
- - Mobile App for hunting rogues even if mobile
Assess
- - Wireless deep packet inspection
- - Behavioral baselining, analysis and anomaly detection/alerts
- - DVR-like capabilities for forensics, including geo-positioning
- - Carrier integration with cell. devices for anomaly detection, fraud/theft and cost management
Respond
- - List and map devices on dashboard or into SIEMs.
- - Interact with MDM and EMM assets for correlation and feedback on exceptions
- - Rectify network segmentation via interactions with SOAR, FW and/or NAC systems
- - Automate response and closure via collaboration with ITSM/ITSL and CMDBs