Uncover the Hidden Dangers:
The Urgent Need for Robust Wireless Airspace Defense
AI-Enabled Signal Intelligence

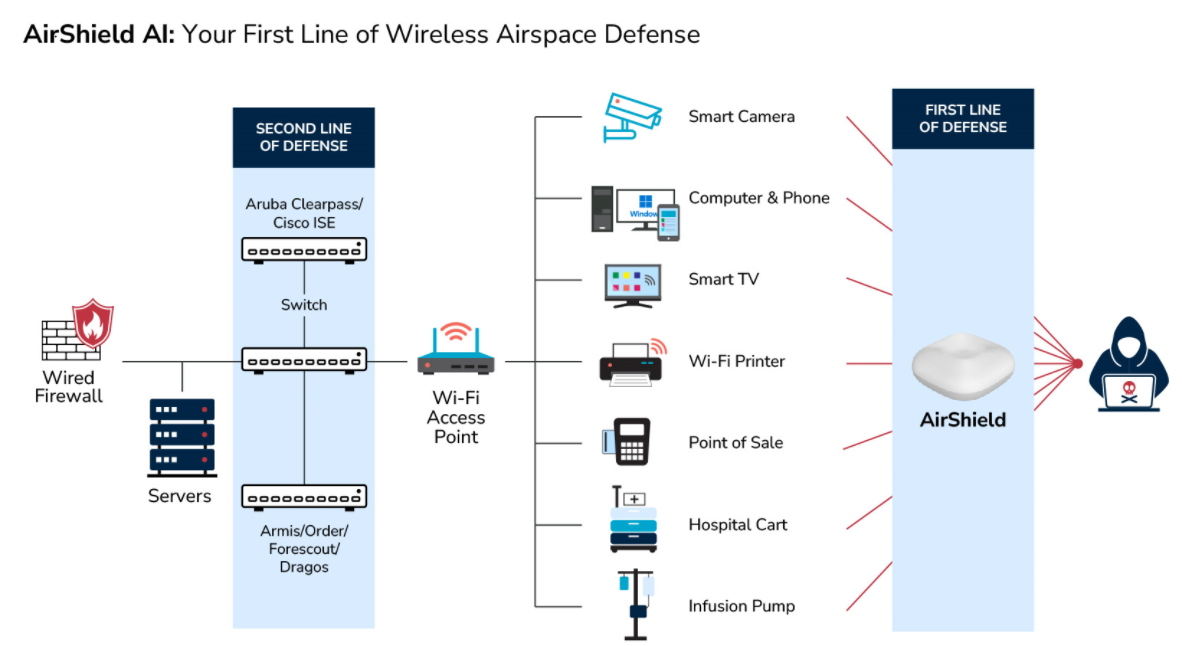
What is Wireless Airspace Defense?
Wireless Airspace Defense is a next generation RF visibility threat detection and mitigation platform that focuses on securing layer 0, 1, and 2 before an IP is assigned.
The explosive growth of connected devices presents a complex challenge for organizations.
Wireless Airspace Defense addresses these threats and vulnerabilities through multi-tier solutions.
LOCH Founder and CEO Garry Drummond explains the critical role Wireless Airspace Defense plays in modern network security systems

Join Us at the Security & Policing Home Office Event – Farnborough, UK, March 11th - 13th, 2025
Read More
Creating the Next Frontier in Wireless Technology: The Critical Need for Wireless Airspace Defense
Read More
The Silent Threat of Rogue Wi-Fi Networks on Navy Ships – How LOCH's AirShield Could Have Prevented a Security Breach
Read More
Strengthening National Security with LOCH AirShield Wireless Airspace Defense and ACS - Autonomic Cybersecurity: Mitigating the Risks of Chinese Maritime Cranes
Read More
Advancing the Future of Cybersecurity with Resilient Machine Learning Systems (rMLS) to Protect Artificial Intelligence and Machine Learning from Cyberattacks
Read MoreBenefits of Using SDR for Cybersecurity
Benefits of Using Wireless Airspace Defense for Cybersecurity
Real-Time Threat Detection
SDRs enable real-time monitoring and analysis of wireless signals, providing the ability to detect and respond to threats such as unauthorized transmissions, jamming, and signal spoofing as they occur.
Comprehensive RF Visibility
AirShield provides real-time visibility of all wireless/RF devices within an environment, regardless of their operating system, protocol, or connection type. This helps eliminate blind spots that can be exploited by attackers.
Safeguard Navigation Systems
Spoofing or jamming attacks can mislead vehicle, aircraft, and smartphone navigation systems, leading to accidents or intentional rerouting. GPS Canary ensures accurate GPS signals reach these systems, providing safe and reliable navigation.
Non-Intrusive Monitoring
AirShield uses passive monitoring techniques, ensuring that it does not interfere with the network while enforcing Zero Trust policies. This makes it easier to integrate into existing systems without disruption.
Comprehensive Spectrum Analysis:
SDRs can analyze a wide range of frequencies and protocols simultaneously, offering comprehensive visibility into the wireless spectrum and helping to identify anomalies and malicious activities.
Broad-Spectrum RF and Cellular Security
The AirShield platform can monitor a wide range of frequencies, from traditional WiFi to the latest 5G network and GPS signals, ensuring comprehensive security coverage across various communication protocols.
Protocol Agnostic
SDRs are not limited to specific communication protocols, making them ideal for environments with diverse wireless technologies, such as Wi-Fi, cellular, Bluetooth, and IoT.
Automated Threat Detection
AirShield uses AI and machine learning to detect, assess, and prevent risks from unmanaged, unsecured, and misconfigured wireless devices, automating the identification and mitigation of potential threats.
Enhanced Situational Awareness
By continuously scanning and analyzing the wireless environment, SDRs provide detailed situational awareness, helping to identify potential security breaches and vulnerabilities.
Ease of Deployment
AirShield is designed for easy deployment without the need for Ethernet connections, utilizing integrated cellular backhaul for real-time access to cloud-based threat analytics.
Cost-Effective Solution
SDRs can replace multiple specialized hardware devices with a single, versatile platform, reducing costs associated with purchasing, maintaining, and upgrading traditional radio equipment.
Real-Time Data Analytics
The AirShield platform offers real-time data analytics and reporting, helping organizations quickly identify and respond to unacceptable wireless vulnerabilities.
Scalability
SDRs can be scaled to cover large areas and high-density environments, making them suitable for protecting extensive wireless networks, such as those found in smart cities and industrial IoT applications.
Customizable Software-Defined Radio
Software-defined radios (SDR) capabilities allow for monitoring and detecting of new and advanced wireless threats, providing a customizable approach to wireless security.
Advanced Signal Intelligence (SIGINT)
SDRs can perform advanced signal intelligence operations, including signal classification, demodulation, and decoding, providing deeper insights into potential threats and malicious activities.
Mobile Threat Hunting Application
AirShield includes a mobile application for on-premise threat hunting, enabling users to locate and remove rogue wireless devices effectively.
Rapid Deployment
SDRs can be quickly deployed and configured to address specific security needs, allowing organizations to respond swiftly to new threats and vulnerabilities.
Integration with Security Systems
The AirShield platform integrates seamlessly with existing security systems such as SIEM, SOAR, and ITSM, providing a unified approach to threat detection and response.
Integration with Cybersecurity Tools
SDRs can be integrated with existing cybersecurity tools and frameworks, enhancing overall security operations and enabling more effective threat detection and response.
Zero Trust Security Framework
AirShield supports a Zero Trust security framework, which is crucial for managing the security of wireless devices and mitigating the risks of rogue actors and misconfigured devices.
Ready to protect against wireless threats?
Wireless Attack Surfaces are growing at an exponential rate putting organizations at ever increasing risks.
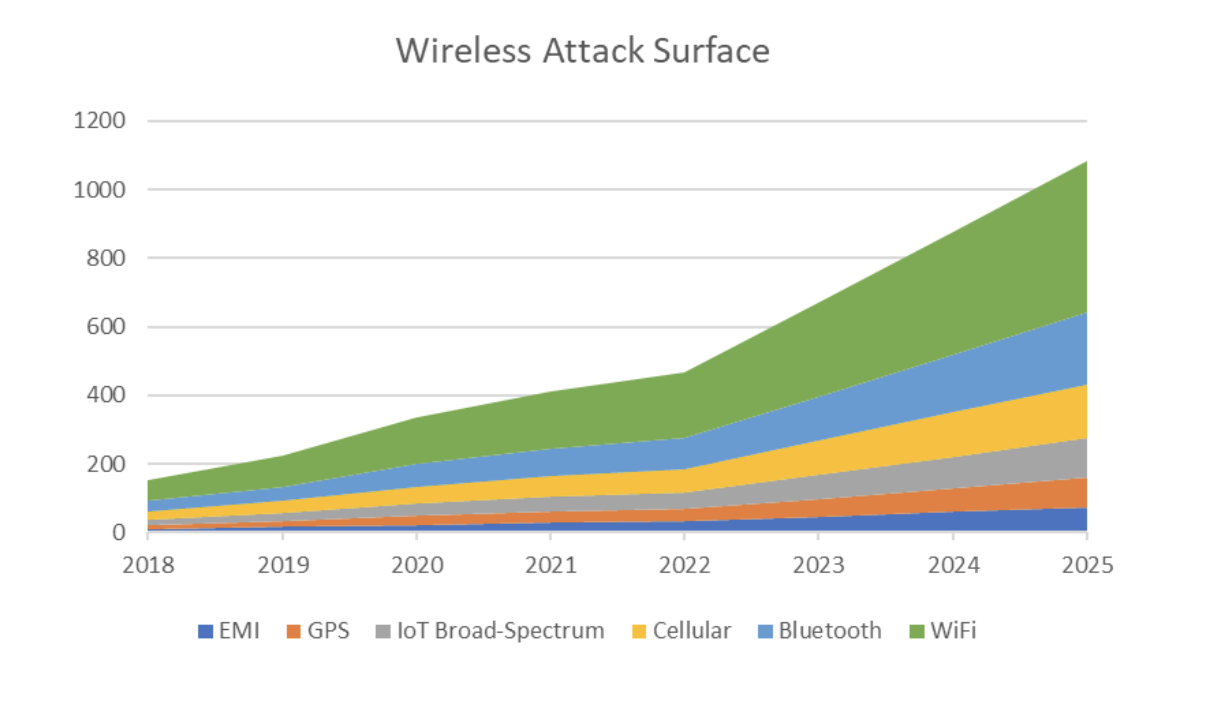
Wireless Attack Surfaces
GPS
GPS, vital for global navigation and oversight, is targeted due to the accessibility of software-defined radios. Attackers manipulate radio frequencies, disrupting accurate timing and location data, impacting critical infrastructure and emergency services relied upon by society and organizations.
CBRS
CBRS, operating in the 3.5 GHz to 3.7 GHz band, faces risks like IMSI catchers, man-in-the-middle attacks, denial of service, downgrade attacks, and protocol exploits. These vulnerabilities enable interception, communication alteration, device tracking, and service disruption, especially in IoT deployments shifting towards CBRS from traditional Wi-Fi networks.
IoT
The Internet of Things (IoT) revolutionizes business with improved efficiency, maintenance monitoring, and communication. However, IoT devices face security vulnerabilities such as unauthorized access and password exploitation. Other risks include weak authentication, insecure communication, lack of updates, and physical vulnerabilities.
Satellites
Satellite technology offers immense benefits yet faces significant threats in terms of cybersecurity. With increasing reliance on satellites for crucial services such as communication and navigation, addressing satellite security concerns becomes increasingly urgent to prevent potential cyberspace warfare and protect essential infrastructure.