Don’t hand it Over: Vulnerabilities in the Handover Procedure of Cellular Telecommunications
New Mobile Network Vulnerabilities Affect All Cellular Generations Since 2G. Researchers have disclosed security vulnerabilities in handover, a fundamental mechanism that undergirds modern cellular networks, which could be exploited by adversaries to launch denial-of-service (DoS) and man-in-the-middle (MitM) attacks using low-cost equipment.
Researchers Evangelos Bitsikas and Christina Pöpper from the New York University Abu Dhabi in their very recent publication highlight how an attacker who sets up a false base station mimicking a legitimate one can utilize the vulnerabilities in the handover procedure to cause serious damage including loss of valuable confidential information, affecting the user as well as the operator.
With the prolific use of cellular infrastructure for data connectivity, especially M2M industrial control systems used in critical infrastructure today, it is imperative to maintain a constant pulse of the radio frequencies in the surrounding air space.
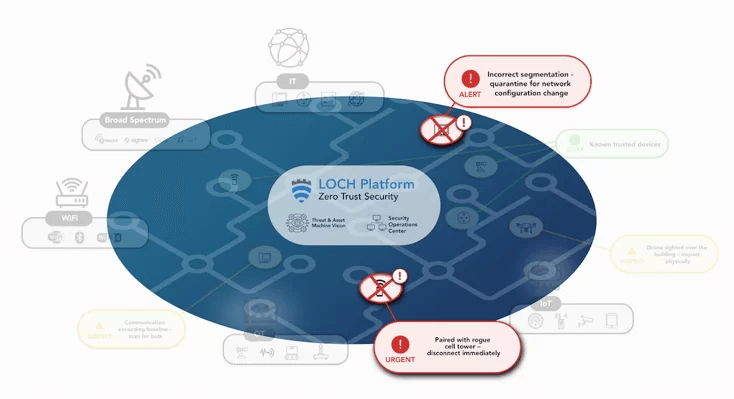
LOCH Technologies programmable software defined radio based AirShield℠ sensors with built in AirCell℠ were specifically designed to sniff out false or rogue cell towers the moment they show up in the environment.
With 80% of IoT devices now wireless, and IoT creating the world's largest attack surface, wireless is the new network and attack surface combined. This reality has created two critical security gaps that you need to be concerned about. The first is understanding your airspace of today - WiFi and Bluetooth, on and off-network, shadow networks, device behaviors and more. The second is broad-spectrum wireless IoT, which are things beyond typical WiFi and Bluetooth systems, such as 4G/5G Cellular.
Learn more about the risks and threats associated with wireless technologies and how to implement best practices for wireless zero trust at https://loch.io and watch our video that highlights our wireless machine vision technology.
