Defend the Digital Dock
Wireless Airspace Defense for U.S. Coast Guard 2025 MTS Cybersecurity Compliance
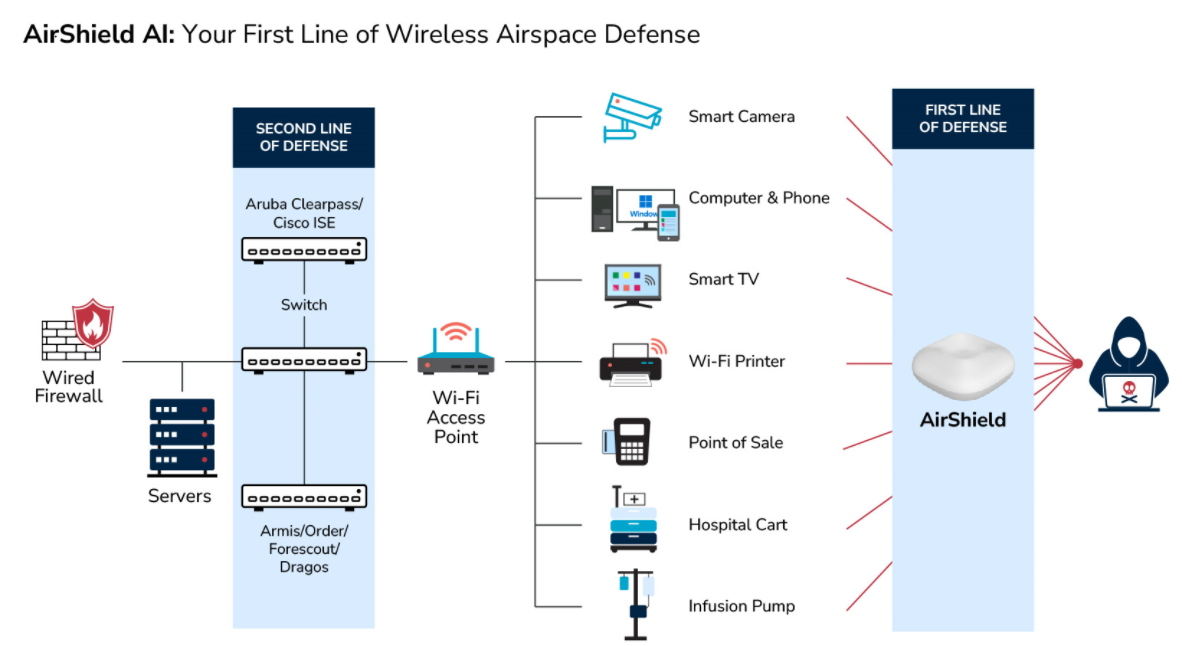
The Growing Problem: The Wireless Blind Spot in Maritime Cybersecurity
The U.S. maritime sector is facing a critical cybersecurity gap—the wireless blind spot. While traditional cybersecurity solutions monitor internal IT networks, wireless-connected devices and signals remain largely invisible, leaving ports, ships, and terminals vulnerable to attack.
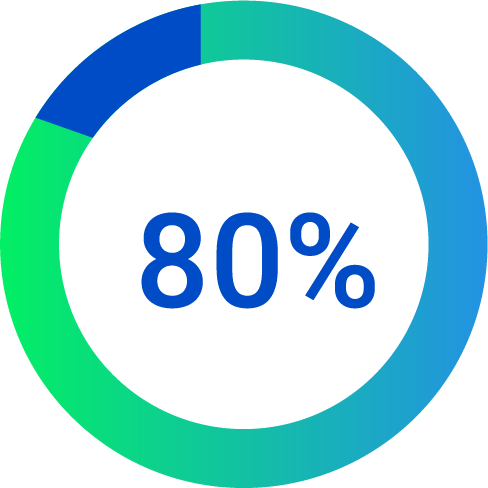
80% of port-side devices now connect wirelessly
Traditional IT tools provide no visibility into wireless activity.
GPS Spoofing, rogue LTE modems, Bluetooth skimmers, and RF jammers are being used for cyber-physical disruption.
These threats can interfere with OT systems, leading to operational downtime, lost cargo, and even vessel collisions.
Protect Your Port & Stay Compliant with the Latest USCG Standards

Join Us at the Security & Policing Home Office Event – Farnborough, UK, March 11th - 13th, 2025
Read More
Creating the Next Frontier in Wireless Technology: The Critical Need for Wireless Airspace Defense
Read More
The Silent Threat of Rogue Wi-Fi Networks on Navy Ships – How LOCH's AirShield Could Have Prevented a Security Breach
Read MoreBusiness Impact: Downtime, Fines, and Non-Compliance
The cost of ignoring Wireless Threats
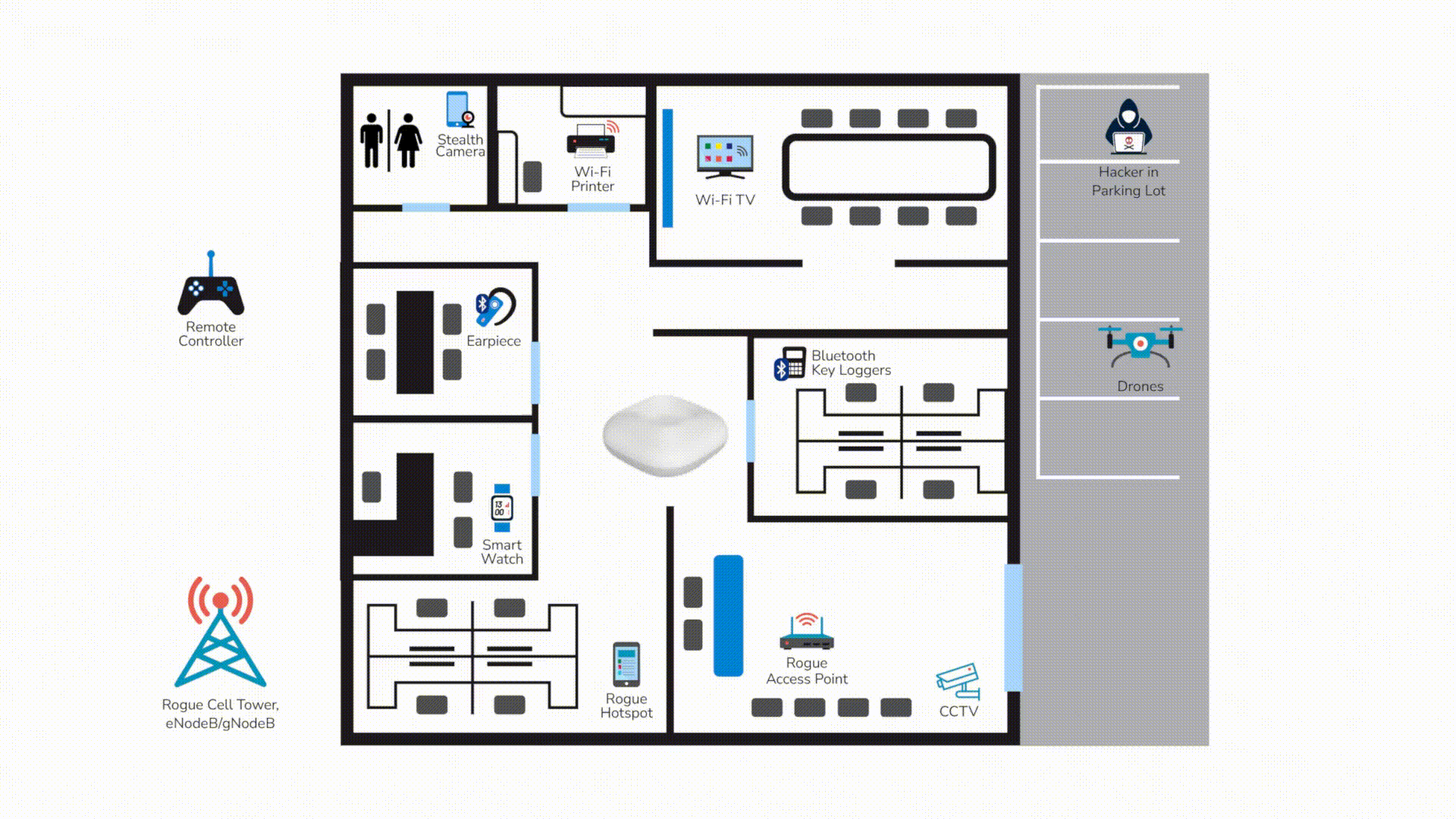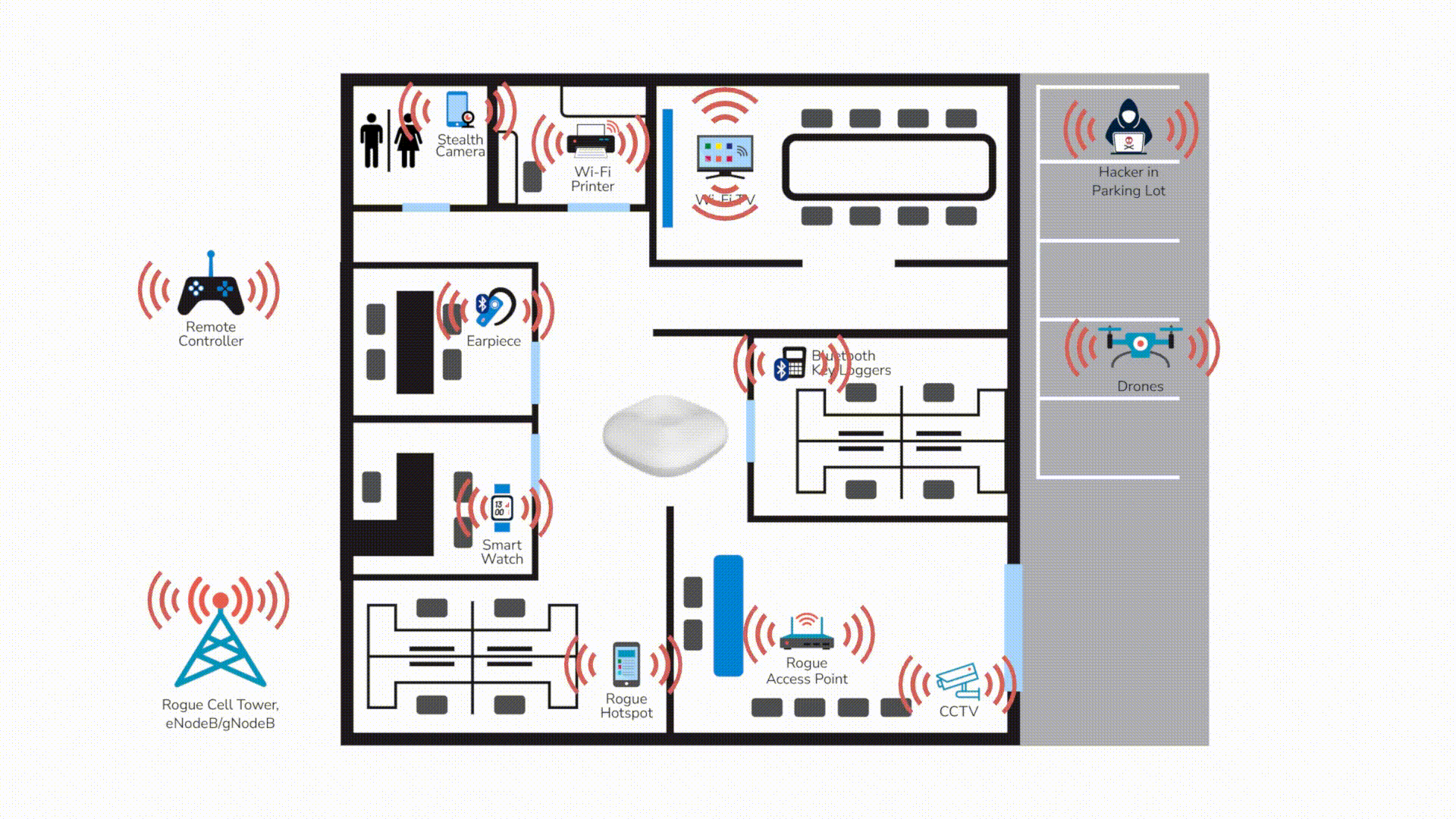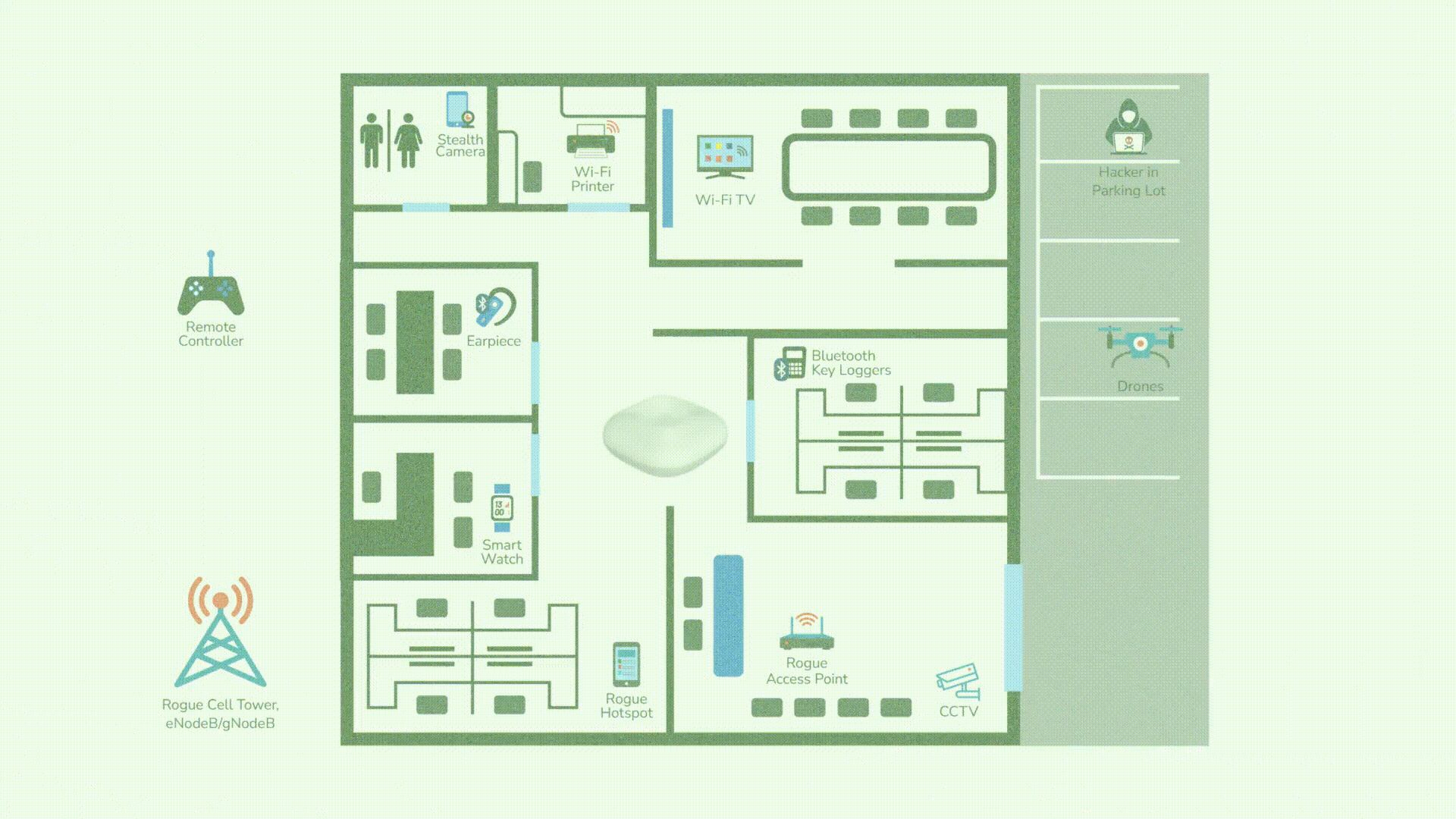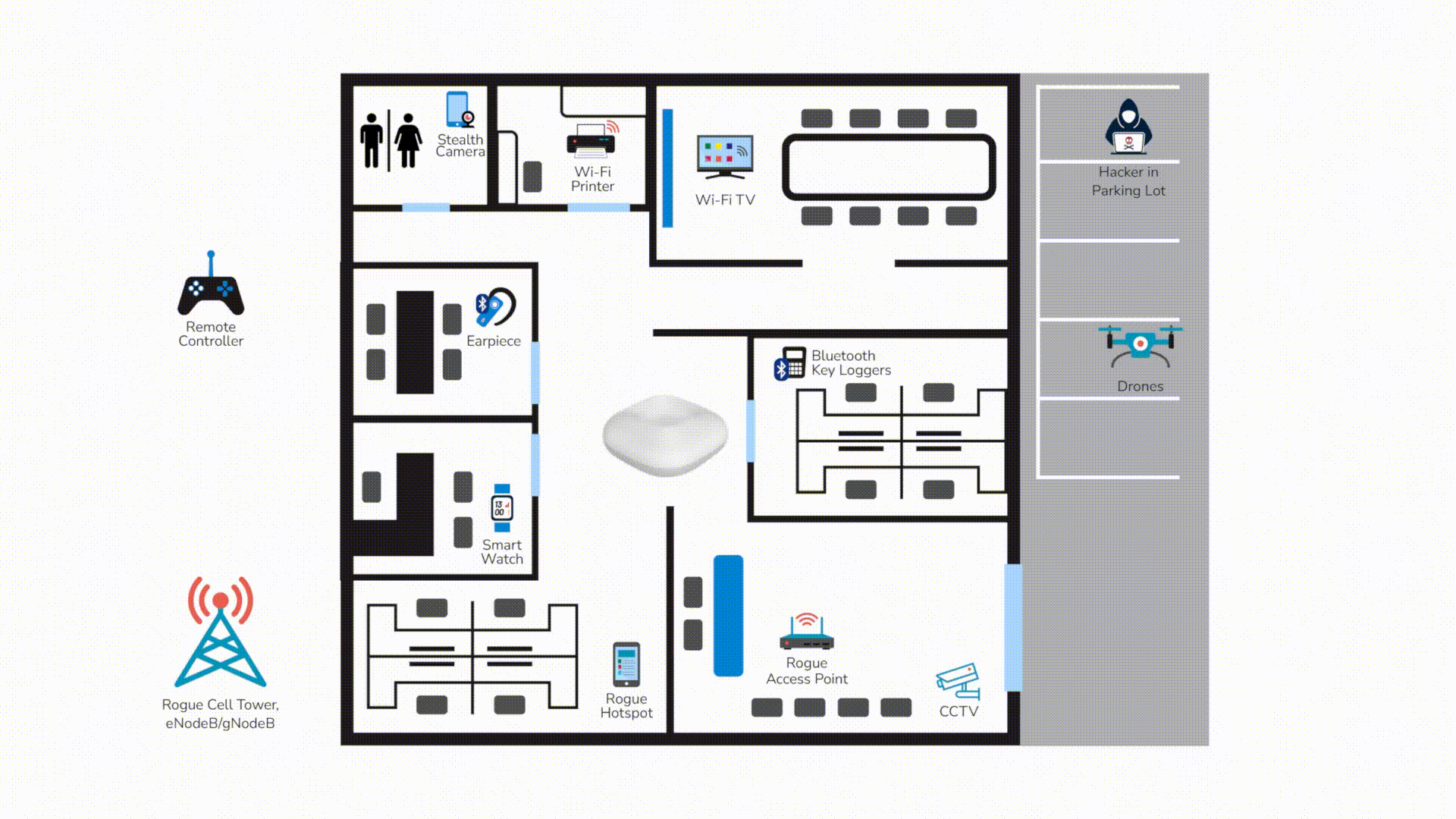
Rogue Access Points
Enable covert intrusion into OT systems
GPS Spoofing
Causes navigation errors, vessel grounding, and cargo delays
Unmanaged Wireless/IoT Devices
Creates backdoors for attackers via BYOD or third-party devices
RF Jamming or Signal Interference
Interrupts port logistics, ship communications, and safety systems
Lack of Continuous Monitoring
Results in failure to meet 33 CFR 106 cybersecurity mandates
No Forensic Data
Makes it impossible to investigate, respond, or demonstrate compliance during audits
Regulatory Urgency: USCG's 2025 Cybersecurity Rule (33 CFR 106)
- Baseline cyber risk assessments
- Continuous cybersecurity monitoring
- Incident response plans
- Documentation and audit readiness
- Enforcement of cybersecurity procedures and controls
These requirements explicitly extend to wireless and RF-based cyber threats - an area unmonitored by most maritime cybersecurity stacks today.
Ready to learn how to protect your port?
Real-Time RF Detections
From rogue APs to fake GPS towers
Zero Trust Enforcement
Across all wireless communications
SIEM/SOAR/CMDB Integrations
For response and compliance logging
Cloud + On-Prem Deployment
Built for critical infrastructure flexibility
Detect, Track, and Remediate
Mapping LOCH to the USCG 33 CFR 106 Cybersecurity Requirements
| USCG Rule | LOCH Capability | Mapped Compliance Area |
|---|---|---|
|
106.230 Cyber Risk Assessment
|
AirShield discovers and classifies all RF-Connected devices
|
Asset Visibility
|
|
106.235 - Cybersecurity procedures and control
|
Zero Trust Policy enforcement, real-time anomaly detection, GPS spoof/jam detection
|
Zero Trust Implementation
|
|
106.240 - Incident Response Plan
|
AI-driven threat detection, RF forensic logging, SIEM/SOAR integration
|
Incident Response
|
|
106.245 Documentation & Compliance
|
Centralized dashboards, audit-ready reporting, CMDB/NAC integrations
|
Audit Readiness
|
|
106.250 Continuous Monitoring
|
Persistent RF monitoring from 300 MHz-6 GHz
|
Continuous Wireless Monitoring
|
|
Implicit - Vulnerability Management
|
Identification of rogue devices, misconfigured wireless assets, tampered IoT hardware
|
Risk Mitigation
|
|
Implicit - Supply Chain Threat Detection
|
Exposes embedded threats in third-party wireless equipment
|
Supply Chain Risk Management
|
LOCH's Wireless Airspace Defense Provides Sector-Proven Value
LOCH Technologies Wireless Cybersecurity Solutions