UK Government introduced Product Security & Telecommunications Infrastructure (PSTI) Bill to strengthen IoT Security

SOURCE: Ryan Daws, TechForge Media, 25th Nov. ‘21
Enforcement is to be conducted by a yet-undetermined regulator that will have the power to fine companies for non-compliance up to £10 million or four percent of their global turnover. They will also be able to fine up to £20,000/day for ongoing contraventions.
Amongst the many mandatory requirements is the ban on default passwords, which are easy targets for cybercriminals. The use of default or simple passphrases are still prevalent in many WiFi manufacturers’ solutions ranging from newly IoT devices to media players to printers to personal hotspots.
LOCH’s AirShield Wireless IoT asset management & cybersecurity protections cover 802.11 and Bluetooth/BLE devices as well as those connected via 4G/5G and broad-spectrum radio frequencies (300MHz to 6GHz); and provide the ability to continuously validate compliance for passwords.
The AirShield software defined radio sensor captures and stores WPA/WPA2 Pre-Shared Key (PSK) handshakes as they are observed in an airspace. These handshakes include the encrypted authentication passphrase used between a wireless network and client, which must be shared to all devices wanting to connect to the network.
While most infrastructure networks today use 802.1X/EAP to require username/password or client X.509 certificates to authenticate, many more still rely upon the shared passphrase for convenience. A common security practice is to rotate this passphrase regularly which can be difficult for many to do, leaving the network vulnerable.
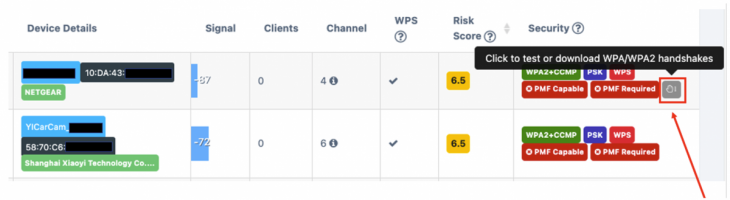
Within our dashboard, collected PSK handshakes are shown with a hand icon for each Access Point. These are collected by the AirShield and the PSK passphrase is tested against a common list of known default and easily-guessable works. Any successful automatic recovery is reported for an actionable response such as changing the passphrase or removing the offending device.
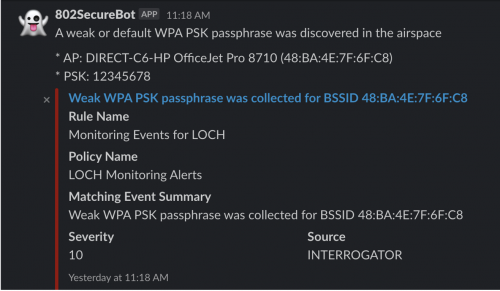
Additionally these handshake files are deliverable in HCCAPX format to download for offline recovery.

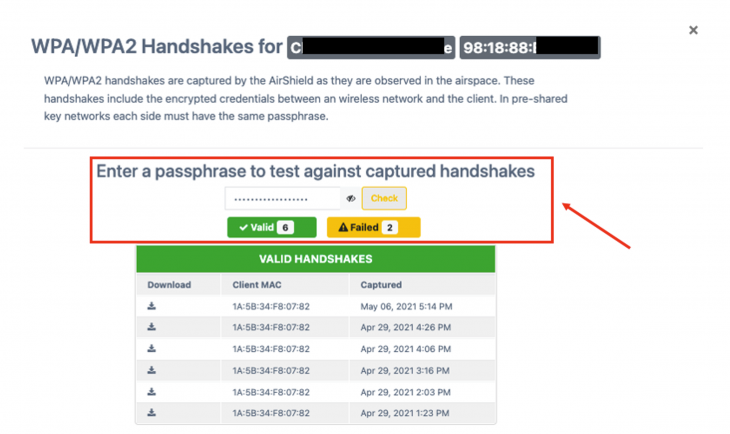
Our dashboard also allows on-line testing of a passphrase against all collected handshakes for an Access Point. This provides a direct audit ensuring a known weak device’s passphrase has been changed or validate devices that went through a factory reset and as such the default passphrases were reinstated.
Contact us for a free broad spectrum wireless assessment – https://lp.loch.io/vulnerability_assessment_offer
https://iottechnews.com/news/2021/nov/25/uk-introduces-psti-bill-to-protect-iot-devices/
