Colonial Pipeline Ransomware Attack: The Urgent Need to Secure Internet-Connected Infrastructure from New Threats
On May 7th, reports surfaced that Colonial Pipeline, operators of the country’s largest fuel pipeline, were impacted by a ransomware attack from hackers linked to Eastern European hacking group Darkside. The company was forced to shut down operations to prevent malicious software from spreading across its network, which immediately impacted gasoline and jet fuel supply across the East Coast. Ultimately, the Colonial Pipeline was forced to pay $5 million in ransom money to regain control of its disabled computer network. All things considered, this was a relatively low price to pay, considering the average ransomware price has climbed 311% in the past year alone.
Still, the damage is lasting — and not just for the company’s reputation, but for the growing realization that malicious actors can successfully hack and blackmail major U.S. infrastructural players with relative impunity. In all likelihood, we will continue to see the cyberwar escalate against organizations in sectors like oil and gas, manufacturing, water, and nuclear.
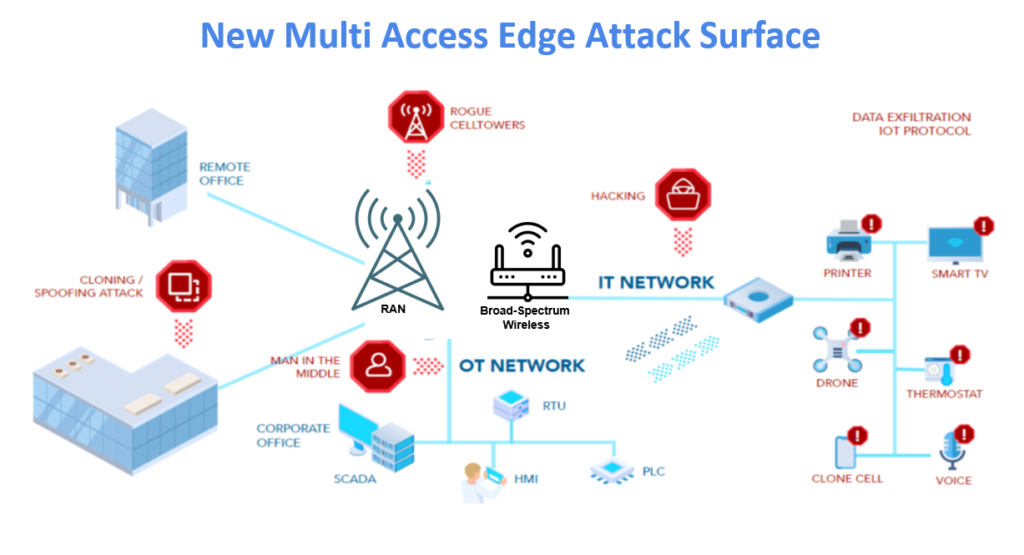
The Colonial Pipeline attack shows that the cybersecurity industry needs to lend additional support to critical infrastructure and utility organizations. The challenge, for these companies, is that aging infrastructure systems are being increasingly connected to the internet, either directly or via the IT network. Moreover, the lines are fastly blurring between traditional IT and OT/ICS/SCADA systems — meaning that even in highly segmented networks, there are ways to bypass traditional security protections to gain access to operational systems. In the case of Colonial Pipeline, it is likely that hackers first gained access through the administrative networks, before eventually reaching and compromising OT computer systems with malware.
It is possible that Darkside-affiliated hackers had access to Colonial Pipeline networks for weeks, if not months, prior to the attack. Part of the challenge, in complex infrastructure settings, is that operators have limited visibility into all of the internet-connected devices and systems — particularly wirelessly operated devices, ranging from IoT sensors, mobile phones/tablets, to third-party IoT devices — that are in the environment and can connect to multiple networks. This is particularly true with the emergence of technologies like multi-access edge computing (MEC), which present the opportunity for malware to traverse over numerous other internet-connected pipes, like cellular and broad-spectrum IoT wireless which are themselves connected to scores of wireless devices.
In general, there are numerous wireless attacks and exploits — from poor authentication, to weak encryption, to man-in-the-middle attacks — that can be used to access core ICS and SCADA systems. In many cases, the only thing that stands between infrastructure companies, their networks, and ransomware attacks are vulnerable, internet-connected IoT sensors that can be used to access critical systems.
For more information on this threat landscape and strategies operators like Colonial Pipeline to prevent attacks, please see our Whitepaper: The Emerging IoT Security Crisis.
For a free LOCH assessment of the wireless threats that exist in your infrastructural or manufacturing environment, sign up for our Free IoT Broad Spectrum Wireless Assessment.
