Product Updates
New AirShield Fixes and Features - June 14, 2024
Can you believe it's 2024 already? We certainly can! During the past year, the LOCH team has been working diligently on a number of features and bug fixes to our platform. Here's a summary of the more notable things!

New Feedback and Support Channels
Our existing Freshdesk environment still is the best place to find documentation and open support tickets. We have opened up the knowledge base to https://my.loch.help as well.
In addition to Freshdesk, you can now submit feedback when you come across a bug or think of a feature you'd love to see! At the bottom left of the console and the right side in localview will be a Feedback button. Click it to bring up our Userback system!
From here you can record a video, including sound, to detail what happened and take and edit a screenshot to highlight areas for us to note.
We appreciate any and all feedback as it is reviewed and responded to via the Userback system and through email.
New Cellular Threat Map
As part of our path to update our user interface, we began with our threat map pages, specifically AirCell's Cellular Threat Map. This new page provides a more user-responsive experience, allowing selected sensors and carriers to be filtered.
We have been expanding our AirCell capabilities in AirShield to support more bands and more details of visible cellular towers. Worldwide coverage, CBRS/Private LTE (Band 48), and more improvements are available to new and renewed customers. Contact your sales representative for details!

Bluetooth Trackers, Spammers, and Rogues, OH MY!
An updated Bluetooth scanner has been released that identifies additional types of BLE broadcast traffic, specifically:
- BLE Trackers, such as Apple AirTag and Tile
- Flipper Zero
- Apple iOS Crashes and Message Spamming
- Windows Message Spamming
- Android Message Spamming
WiFi 6E and 6GHz Spectrum Collection
We fully support WiFi 6-enabled Access Points and are readying support for the new WiFi 7 (802.11be) changes. An updated AirShield hardware to support data collection from the 6 GHz spectrum used by 6E and 7 is available for renewals and new installations!
ISM Signals
Under the IoT section, a new ISM Signals page is now available. To us, ISM Signals represent broadcast transmissions from devices that have a very specific purpose, such as a temperature gauge, power status, and the like. Typically these devices utilize the Industrial, Scientific, and Medical frequency bands, aka ISM, to transmit.
Much like LrWPAN transmissions are typically brief in time and can occur across a wide range of the spectrum, not every signal can be captured. We still believe that a continued monitoring approach that captures some of the data is more valuable than not knowing about the signals.
If questions about a collected ISM Signal arise, please submit feedback or open a ticket through the Help button at the bottom right.

Captured ISM Signals

Apple Wireless Direct Link
You may have already noticed a new section under WiFi for Apple Wireless Devices. Here you'll see a list of all AWDL-supported devices advertising themselves in the 802.11 airspace. Typically this is where you'll find devices like MacBooks, iPhones, and iPads with AirDrop enabled or AppleTVs or other media players with AirPlay enabled.
AWDL works alongside standard IEEE 802.11 and is a method for devices to establish a communication link without having to use the standard AP/STA configuration. In many cases these devices will NOT be visible to your existing systems, flying completely under current network monitoring tools.
By showing you any advertising devices you can now gain a stronger foothold in protecting your airspace.
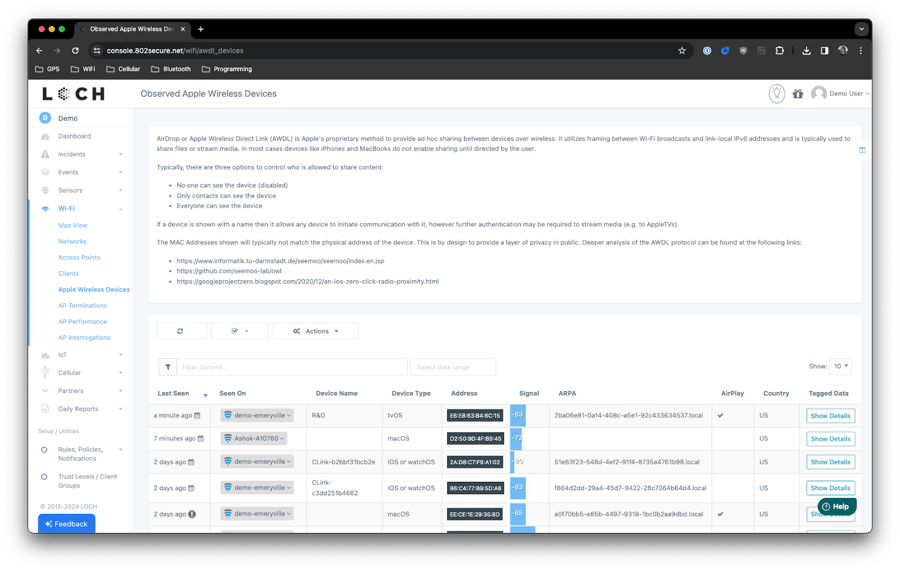
View the list of current and past AWDL devices
Gain historical insights of an AWDL Device
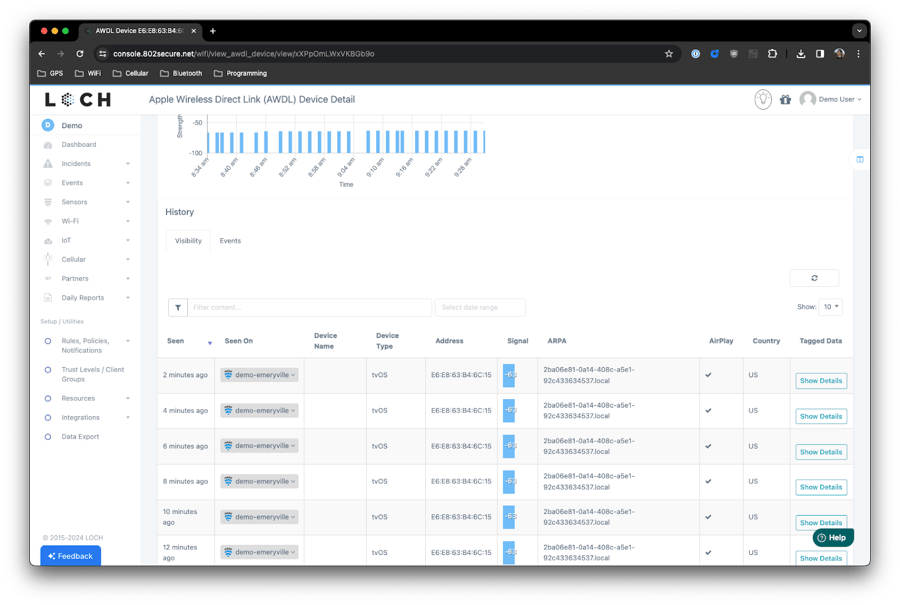
View the history of a visible AWDL device
This information extends to our Localview interface, accessible when you have direct TCP/IP access to an AirShield:
View details of nearby AWDL Devices
Wireshark Decodes
We understand that sometimes additional information about an Access Point or WIDS event may be desirable to truly understand a risk or threat to your airspace. This is why we started to provide the most recent 802.11 Beacon frame and the relevant frame that sparked certain WIDS event, such as an invalid Deauthentication code.
This frame can be downloaded and opened in Wireshark or viewed as a text output through the primary console interface:
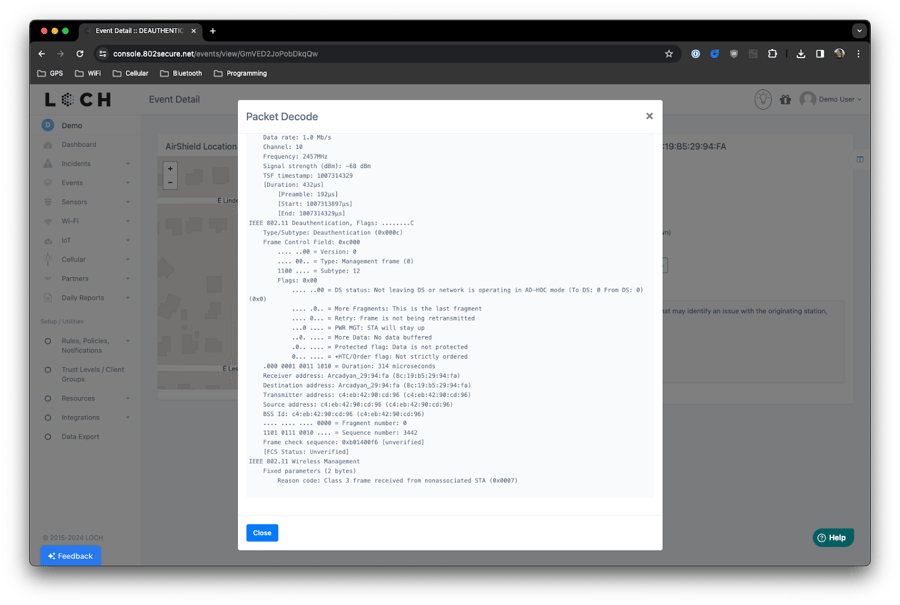
View the details of the 802.11 frame

View a Wireshark decode of an 802.11 Beacon frame
LocalView Updates
LocalView and the AirShield Terminal User Interface (TUI) have been shown a fair bit of attention. Access to the TUI, which allows configuring the AirShield's network interfaces and viewing the current status of services, can be accessed through the serial port using an RJ45 to USB or DB-9 serial cable or via SSH. Contact support for information.
The LocalView Web User Interface (WebUI) can be reached through your browser via the Ethernet's IP Address. Click on the Open Localview icon (a monitor) from the Sensor List view or in the AirShield detail popup for directions.
LocalView is only accessible to Ethernet-connected AirShields.
Download a stream of 802.11 packets for up to 5 minutes
Download historical captured 802.11 packets
WiFi Packet Captures
Directly from an AirShield through Localview you can now download current observed 802.11 frames or historical data as captured. Note that AirShield hops across multiple WiFi channels which may limit full analysis of a WiFi environment. In a future update, we will include the ability to dwell on a specific channel.
Captured data does not persist when the AirShield reboots or loses power.
LocalView Collected Data Downloads
We've heard that having more access to real-time or "off the console" data is something you want. So here we go! From within the AirShield Localview interface, you can now download any or all collected data. Access this from the top right clicking the user icon and then Export Data.
Download AirShield Data in CSV or JSON.
Download a single table in CSV or JSON.
Spectrum Waterfall of WiFi Channel 11
Spectrum Waterfall
Updated AirShields with a Software Defined Radio now have the ability to monitor any part of the RF spectrum with a waterfall view in localview. Please contact your direct sales representative or send an email to sales@loch.io for more information.
runZero Partnership
We are integrating runZero with our platform for our customers. We will provide a seamless method to deploy and manage runZero explorers to facilitate a direct integration between the "wired and wireless" boundary. Contact your direct sales representative or send an email to sales@loch.io for more information.
Visibility across Managed and Unmanaged devices
August 22, 2024 Updates
DEFCON 30 and Beyond!

What a DEFCON!
Hope everyone who was able to attend Blackhat and/or DEFCON had a good time. We certainly did! Always great to see old friends, learn what new tricks are being used, and capture tons and tons of data to help improve our platform. Over the next few weeks, we will be reviewing this data and updating the platform as needed. Read about our lessons learned at DEFCON 32.
What's New and Upcoming
We are currently working on improving our ISM Signal detection and the view page to be a little friendlier and more informational. Right now it's a fairly raw data dump view as we didn't want to hide the fact the data exists.
User experience is high on our target list these next few cycles. More data creates more problems so we lowered the number of table rows that can be viewed down to 100. This will both speed up our backend data queries and lower the amount of post-processing required thus increasing viewing speed.
If you would like to post-process your larger data sets please use the Export Data view and talk to us about integrating with SIEMs.
Client-less PMKID Attack
In addition to WPA/WPA2 PSK handshakes, we are close to releasing an update to our WiFi section that will collect PMKID RSN data when we see it during monitoring. These will be tested against our default wordlist and available to download alongside PSK handshakes. This update will also move away from HCCAPX to the WPA*01/WPA*02 format from Hashcat.
As always we appreciate your input! Please use the Feedback button at the bottom left of the console view to submit any issues or suggestions. Documentation is available on our FreshDesk page.
WiFi 6E and 6GHz Spectrum Collection
We fully support WiFi 6-enabled Access Points and are readying support for the new WiFi 7 (802.11be) changes. An updated AirShield hardware to support data collection from the 6 GHz spectrum used by 6E and 7 is available for renewals and new installations!
July 22, 2024 Updates
We hope everyone is having a great summer! We here at LOCH have been busy working on new features and bug fixes. Here are a few notable things from the past few weeks of work:
WiFi Deauthentication Frame Events
802.11 WiFi Deauthentication Frames and Types are now collected and presented in Events. We will review how often these messages are sent and could tweak the collection. The benefit of monitoring these frames is to help identify misconfigured clients, brute force attacks, or other potential issues that may be security-related.
PCAP for WIDS Events
Certain WIDS events now provide a PCAP download of the frame that triggered it. Look for the download button on the Event list or in the Event Detail, where you can also view a JSON-formatted Wireshark decode:

ISM Signals
General ISM signal collection has been pushed out to all AirShields that support it. This will collect signal data typically sent by sensors in the airspace and can help identify the deployment of radio equipment that could pose a security risk. (Fish tanks, anyone?)
Feedback Button
On the bottom left of the console, you may see a button to provide bug details, feature requests, and general feedback through Userback. Please include screenshots and videos to help us improve the product!








