HIPAA mandates incident response plan to maintain compliance

Covered entities must develop a data backup plan, a disaster recovery plan, and an emergency mode operation plan, among other administrative safeguards.
When a security incident occurs, organizations typically want to contain and eradicate the breach as soon as possible. LOCH’s AirShield wireless asset management and cybersecurity protections provide comprehensive coverage for IEEE 802.11 deployments.
Aligned with the need for split second need to isolate problems LOCH has the built-in capability for ‘Access Point Termination’. Sometimes its a unique endpoint (laptop, desktop, server, IoT client, etc.) that has been compromised and it needs to be isolated from the network before the infection spreads. Other times it’s a rogue Access Point (aka WiFi Pineapple) that’s in the environment masquerading as a trusted device and ready to exploit using man-in-the-middle type attacks.
In either situation, the fasted isolation step is to terminate the suspect Access Point or the one that the infected end point is connected with. This is exactly the capability we have built into our dashboard – select the Access Point, click on ‘Termination’ and then select the desired length of time for the Termination to be in effect (up to 720mins). Once the mitigation work is complete and its sooner than expected, one can bring the Access Point back online, irrespective of the original Termination time that was set.
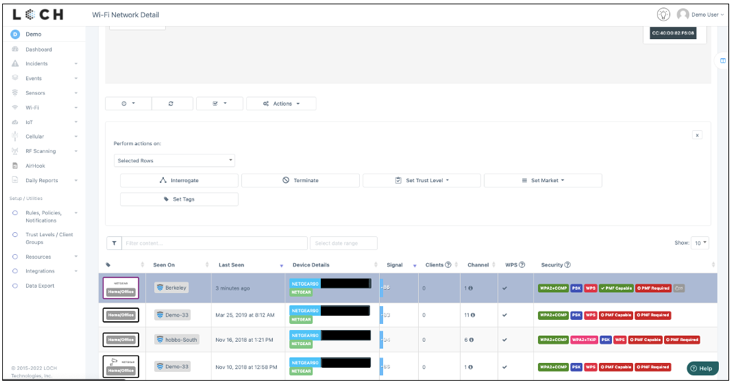
Step 1: Select the AP of interest
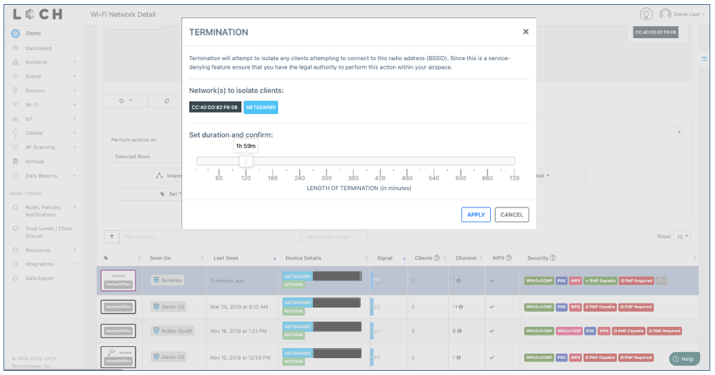
Step 2: Apply termination command with time limit selected
https://loch.io/solutions/healthcare/
#wirelesssecurity #cybersecurity #iotsecurity #infrastructuresecurity #advancedthreatprotection #informationsecurity #informationsecurityawareness #incidentmanagement #socanalyst #incidentresponse #infosec #cyberawareness #cyberdefense #cyberresilience #cybersafety
https://healthitsecurity.com/features/how-to-implement-a-cyber-incident-response-plan-for-healthcare
Related Blog
LOCH CEO Garry Drummond Honored as Entrepreneur of the Year and Most Innovative CEO of the Year 2017 | LOCH Technologies, Inc.
802 Secure Rebrands to LOCH Technologies and Reaffirms Commitment to Securing Cellular and Wireless IoT Devices as Attack Surfaces Increase | LOCH Technologies, Inc.
