LOCH Technologies Wireless Threat Protection
Delivering the next generation AI/ML cybersecurity and threat monitoring for 4G/5G, broad spectrum IoT, IT and OT environments
ZERO TRUST SECURITY
FOR THE NEW MULTI ACCESS EDGE
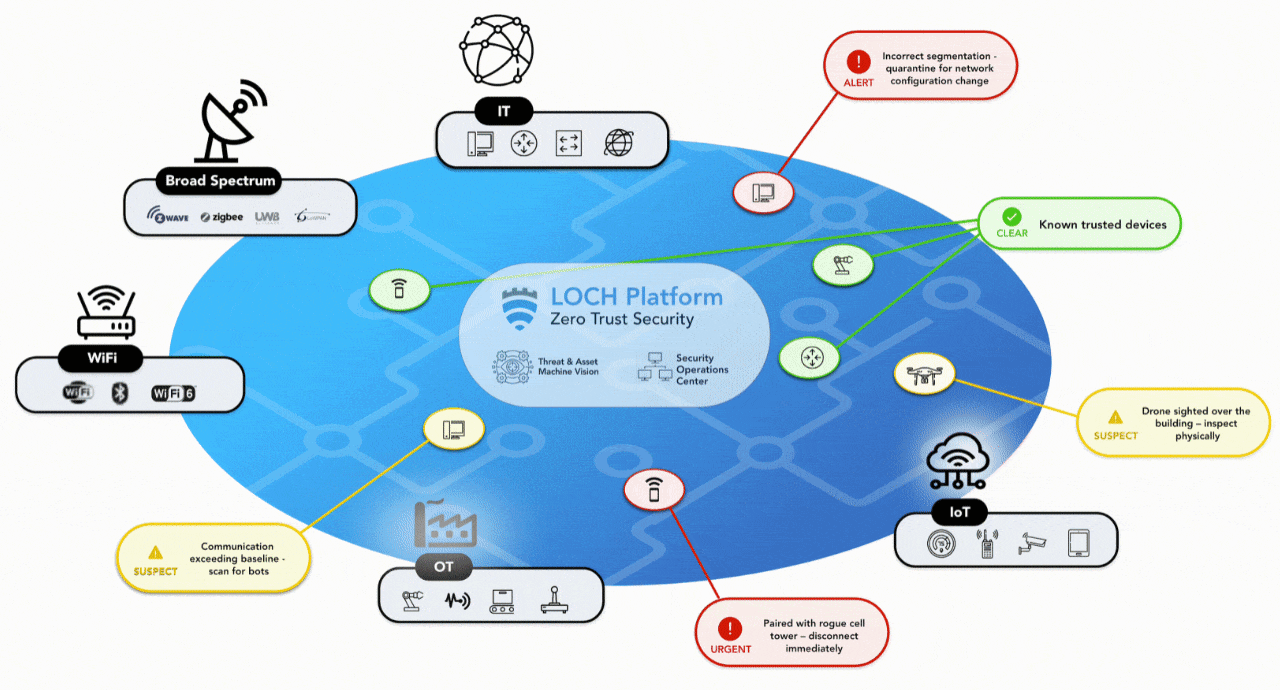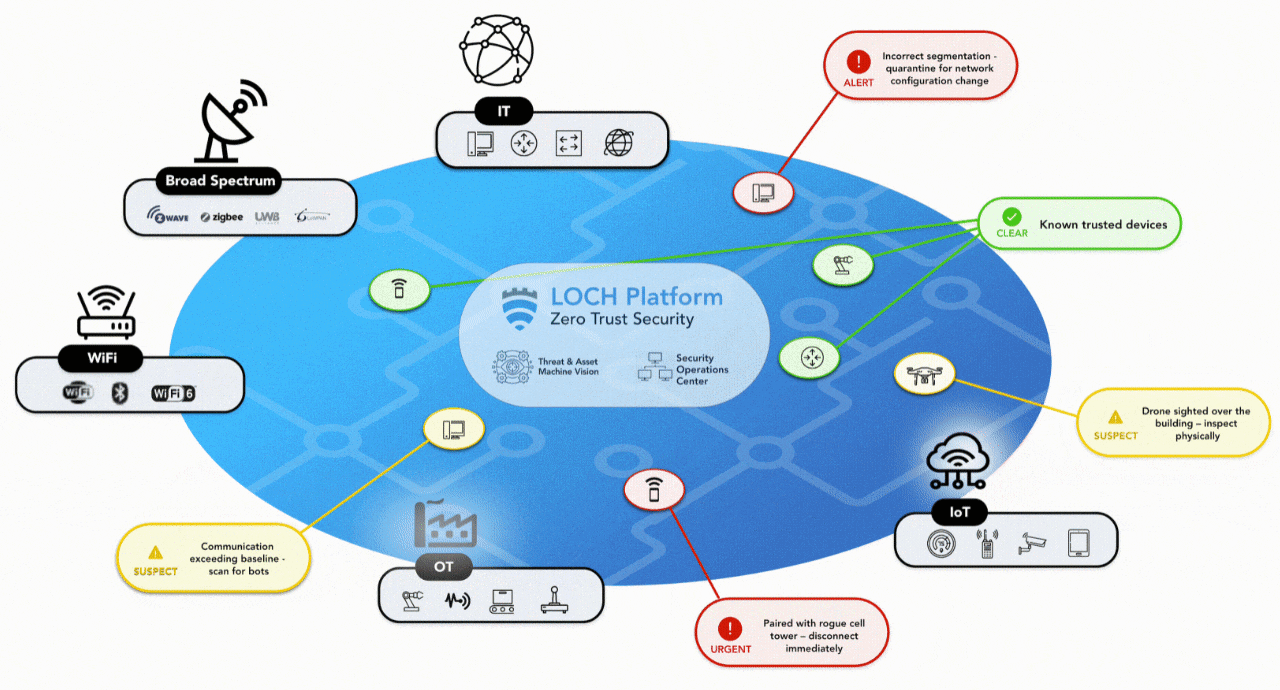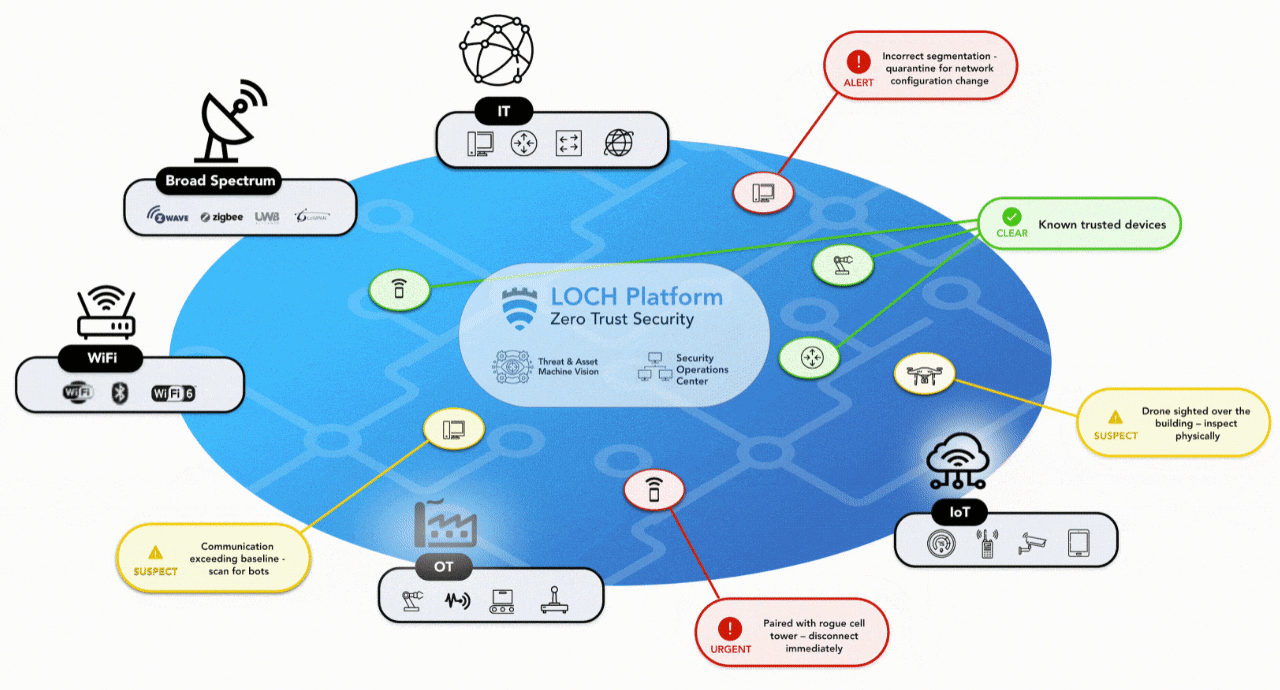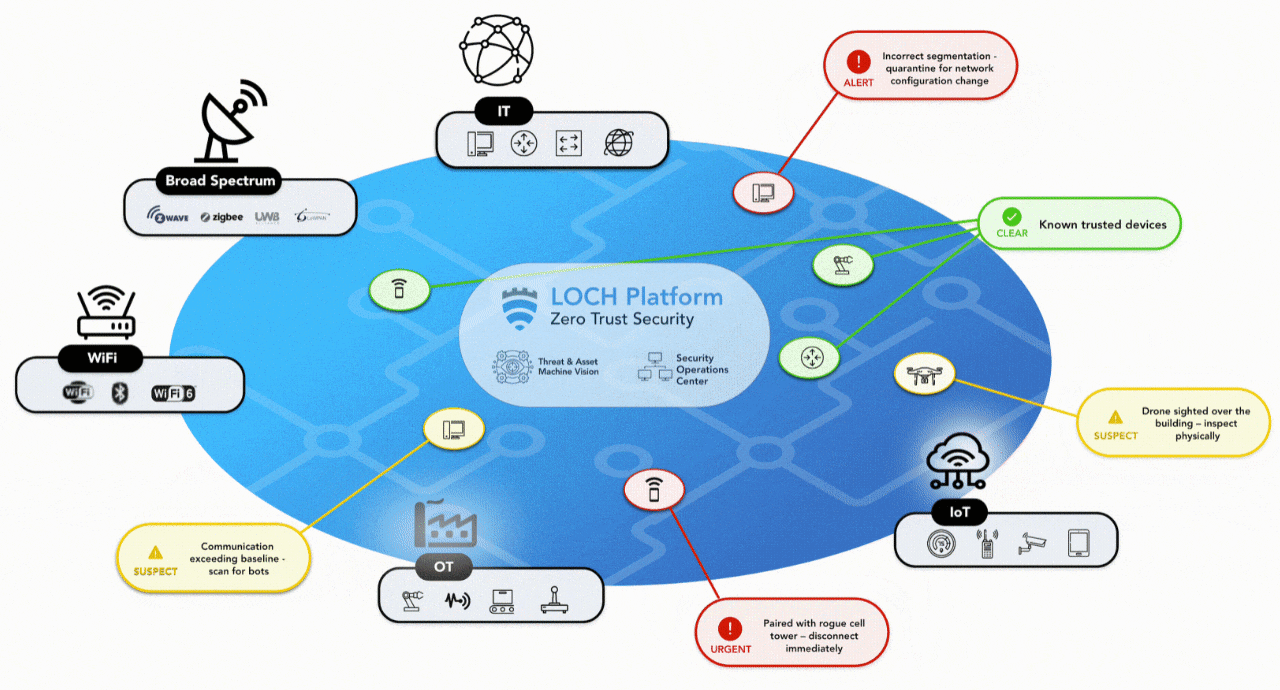
DETECT
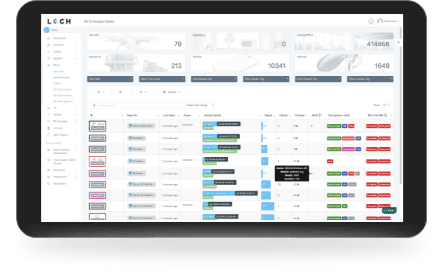
- Detect, identify & classify all broad spectrum RF emitting devices in range
- Device and network pairing communication map analysis and correlation
- Risk assessment threat ranking for Zero Trust network access control
- Mobile App for hunting rogues even if mobile
TRACK
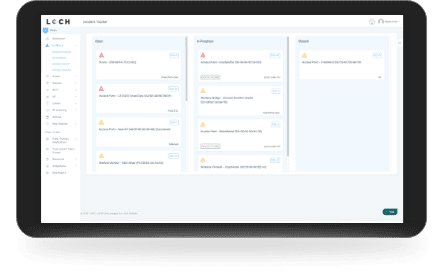
- Wireless deep packet inspection
- Behavioral baselining, analysis and anomaly detection/alerts
- DVR-like capabilities for forensics, including geo-positioning
- Carrier integration with cellular devices for anomaly detection, fraud/theft and cost management
REMEDIATE
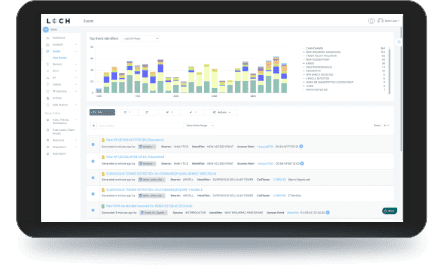
- List & map devices on dashboard or directly into SIEMs.
- Interact with MDM & EMM assets for correlation & feedback on exceptions
- Rectify network segmentation via interactions with SOAR, FW and/or NAC systems
- Automate response & closure via collaboration with ITSM/ITSL & CMDBs
Find out why Gartner® recommends Wireless Airspace Defense for all businesses
LOCH Technologies IoT SECURITY SOLUTIONS

GAMING / HOSPITALITY
Casinos and resorts spread over vastgeographies deal with large volu...
Why Choose LOCH Technologies?
Wireless Airspace Defense platform brings order from chaos
SIMPLE
Easy to deploy on-network or off-network via built-in 4G/LTE
SaaS solution automates discovery of sensor with insights in minutes
Intuitive UI for rules, policies and notification settings
Export raw data APIs, CSV or STIX/TAXII to log aggregators or threat intelligence platforms
COMPREHENSIVE
Software-defined radio
for broad-spectrum RF detection
Protocols – 802.11, Bluetooth, LPWAN, Private LTE & Cellular 4G/5G
Real-time asset inventory, classification and monitoring
Monitoring & behavior analysis for usage, segmentation or isolation
ACTIONABLE
Integration with FW, NAC, SIEM, SOAR & ITSM/ITSL for faster MTTR
Device vulnerabilities and vendor recall or patch status protects brand
Multi-carrier 4G/5G security, performance & cost monitoring
Support Zero Trust initiatives & Compliance for PCI, PHI, NIST and Cybersecurity Maturity Model.








